Partnership with ThreatNG: Your Path to Market Leadership
Are You Still Competing on Price?
Evolve from a commodity service to a strategic partner. ThreatNG gives you the edge to differentiate and dominate the Approved Scanning Vendor (ASV) market.
The Problem
Are your clients flying blind?
Your clients rely on your quarterly scans to achieve compliance, but what about the 90-day window in between? Attackers don’t operate on a quarterly schedule. This "quarterly blindspot" is a significant liability for your clients and a major weakness in your service model.
Is your team drowning in false positives?
The industry-wide problem of false positives is not just your clients’ headache—it’s your business burden.2 Manual validation, re-scans, and a constant stream of frustrated support calls cost your team valuable time and erode client trust.
Is your business trapped by the “Compliance Paradox”?
You are a victim of a system where significant effort is expended on compliance, yet genuine security gaps persist. This "Compliance Paradox" keeps your business transactional, preventing you from becoming a strategic partner.

The Solution
We've built a new path forward—a partnership model that solves your clients’ problems while transforming your business. The ThreatNG platform enables you to offer a superior service that moves you from a "check-the-box" vendor to a trustworthy partner for your clients.
Eliminate the Quarterly Blindspot
Move from a once-a-quarter service to continuous, year-round security. ThreatNG's Continuous Monitoring capabilities ensure you and your clients are always aware of new vulnerabilities and emerging threats, turning a periodic transaction into a continuous security partnership.
Cut Through the Noise with Verified Findings
ThreatNG’s DarCache Vulnerability repository provides a probabilistic estimate of exploitation (EPSS), a list of vulnerabilities actively being exploited in the wild (KEV), and direct links to verified Proof-of-Concept exploits. This enables you to provide your clients with validated findings, thereby eliminating the burden of false positives and allowing them to focus on the real threats.
Find What Other ASVs Miss
Traditional ASV scans often fail due to an incomplete scope. ThreatNG's comprehensive External Discovery uncovers your clients’ entire digital footprint, including forgotten subdomains, unsanctioned cloud services, and third-party vendor connections. This proactive discovery capability helps you deliver a more accurate and valuable scan, reducing scan failures and proving your superior value from day one.
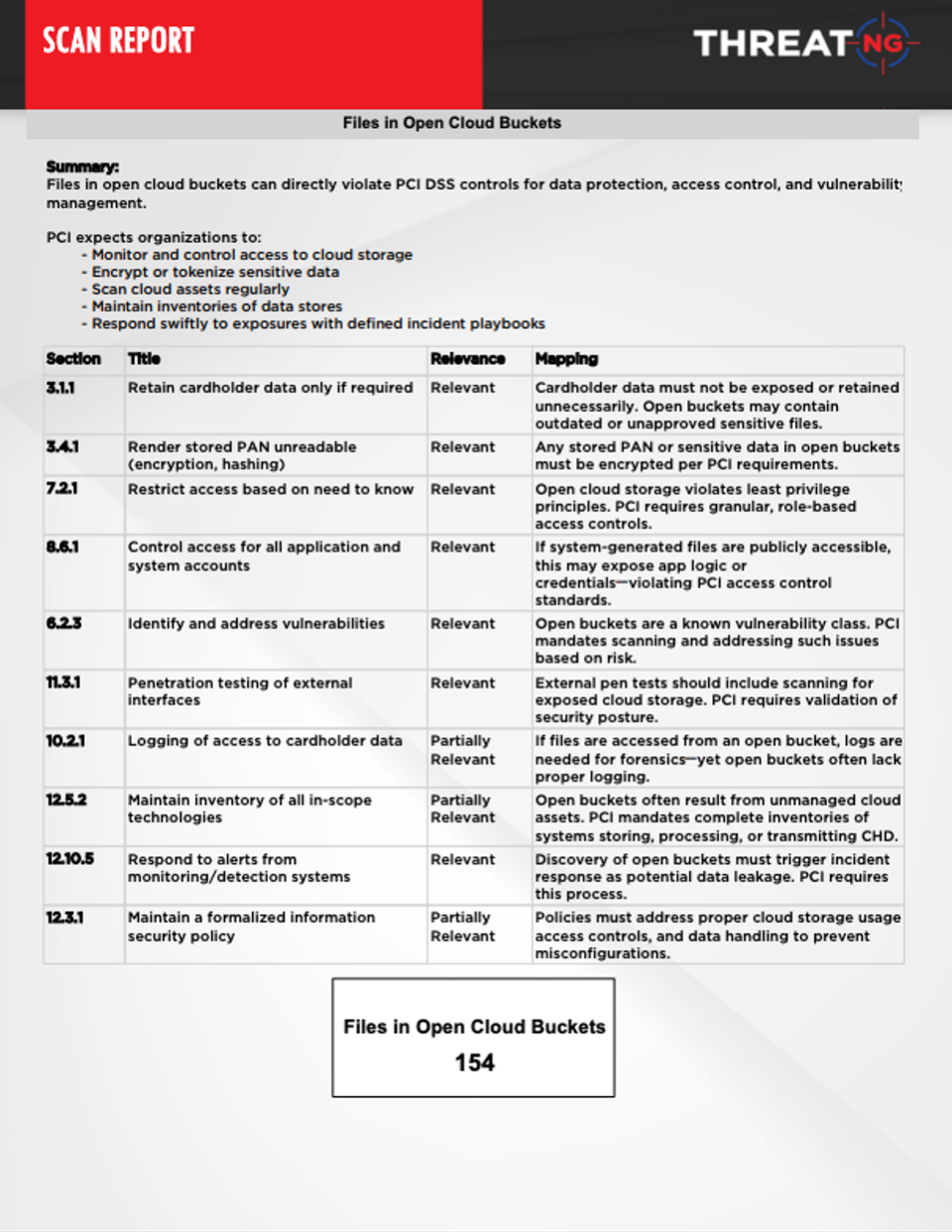
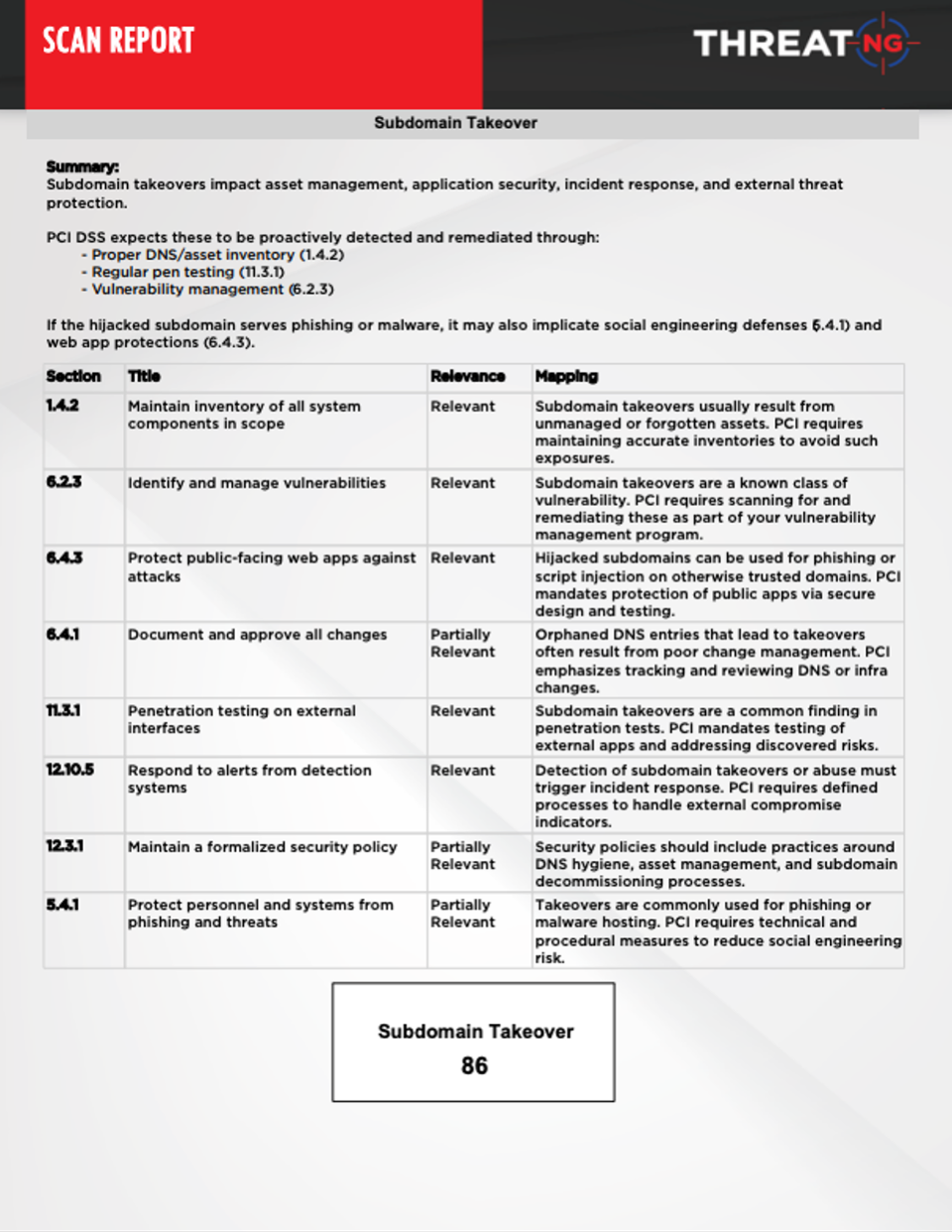
Clear PCI DSS Alignment Through Actionable External Assessments
ThreatNG streamlines your external PCI assessment by providing clear, actionable insights into your security posture from an attacker's perspective. Our easy-to-read reports detail crucial findings, including sensitive information exposed in public repositories, compromised credentials, default port scans, and mentions on the dark web. Each finding is meticulously mapped to relevant PCI DSS requirements, enabling organizations to understand their compliance status and prioritize remediation efforts to enhance their security defenses and protect cardholder data.

Stop Reacting to Compliance Scans, Start Leading the Market:
See How ThreatNG Elevates Your ASV Solution to a Strategic External Risk Platform.
As an Approved Scanning Vendor (ASV), your primary goal is to help clients achieve and maintain PCI DSS compliance. But in today’s rapidly evolving threat landscape, compliance is no longer a differentiator; it’s the baseline. Attackers are looking beyond Requirement 11.3.2 and targeting exposed cloud assets, forgotten code repositories, and brand impersonation domains that your current tools may not see. To truly lead the market and provide clients with the comprehensive security they need, your solution must move from a compliance check to a continuous, proactive external risk platform. Discover how to use ThreatNG’s unified external attack surface management and digital risk protection capabilities to offer unmatched intelligence and secure your status as a strategic partner, not just a scanner. Get a quick demo now and download your strategic blueprint: The Proactive Approved Scanning Vendor: A Strategic Blueprint for Market Leadership with a Unified Discovery Platform.
See a Demo and Request a Free Evaluation
See a demonstration by one of the team members, or click here.
Download Our White Paper
The Proactive Approved Scanning Vendor: A Strategic Blueprint for Market Leadership with a Unified Discovery Platform

Frequently Asked Questions:
A Strategic Guide for Approved Scanning Vendors
For too long, the PCI Approved Scanning Vendor (ASV) business has been stuck in a commoditized market. We understand the frustrations: relentless price pressure, transactional client relationships, and the ongoing struggle to keep customers who view your core service as just a “check-the-box” requirement. These issues are not just standard parts of the business; they indicate a fundamentally broken model that puts both you and your clients at risk. The traditional quarterly scan creates a dangerous “blind spot” for clients between assessments, resulting in a large number of false positives that waste your team’s time and weaken client trust. This FAQ serves as your guide to a new approach, transforming your service from a reactive, low-margin commodity into a high-value, high-retention security partnership through ThreatNG's comprehensive external attack surface management, digital risk protection, and security ratings solution.
For more information, please visit threatngsecurity.com/pci.