External GDPR Assessment
Facing the Fines: The GDPR Blind Spot Your Scanners Can't See
You’ve invested heavily in internal audits and penetration tests to ensure General Data Protection Regulation (GDPR) compliance. You have the reports and the confidence that comes with them. But there is a silent, unmanaged threat that exists outside your perimeter—a sprawling, unmanaged digital footprint that no internal tool can see. This is the "outside-in" GDPR blind spot that an unauthenticated attacker is already probing for right now. ThreatNG's External GDPR Assessment turns that blind spot into clear, actionable intelligence, shifting your posture from reactive auditor to a proactive, resilient defender.
The Problem: Your Internal View Is a Security Blind Spot
Traditional security tools give you an inside-out view, but they miss what's visible to the outside world. This creates a critical GDPR compliance gap, putting you at risk of substantial fines and reputational damage.
Exposed Pains
Your organization may have public-facing assets like an admin page that are not protected, making them a high-value target for attackers. A vulnerability in a subdomain's header could allow an attacker to gain unauthorized access to personal data, violating core principles of confidentiality and integrity.
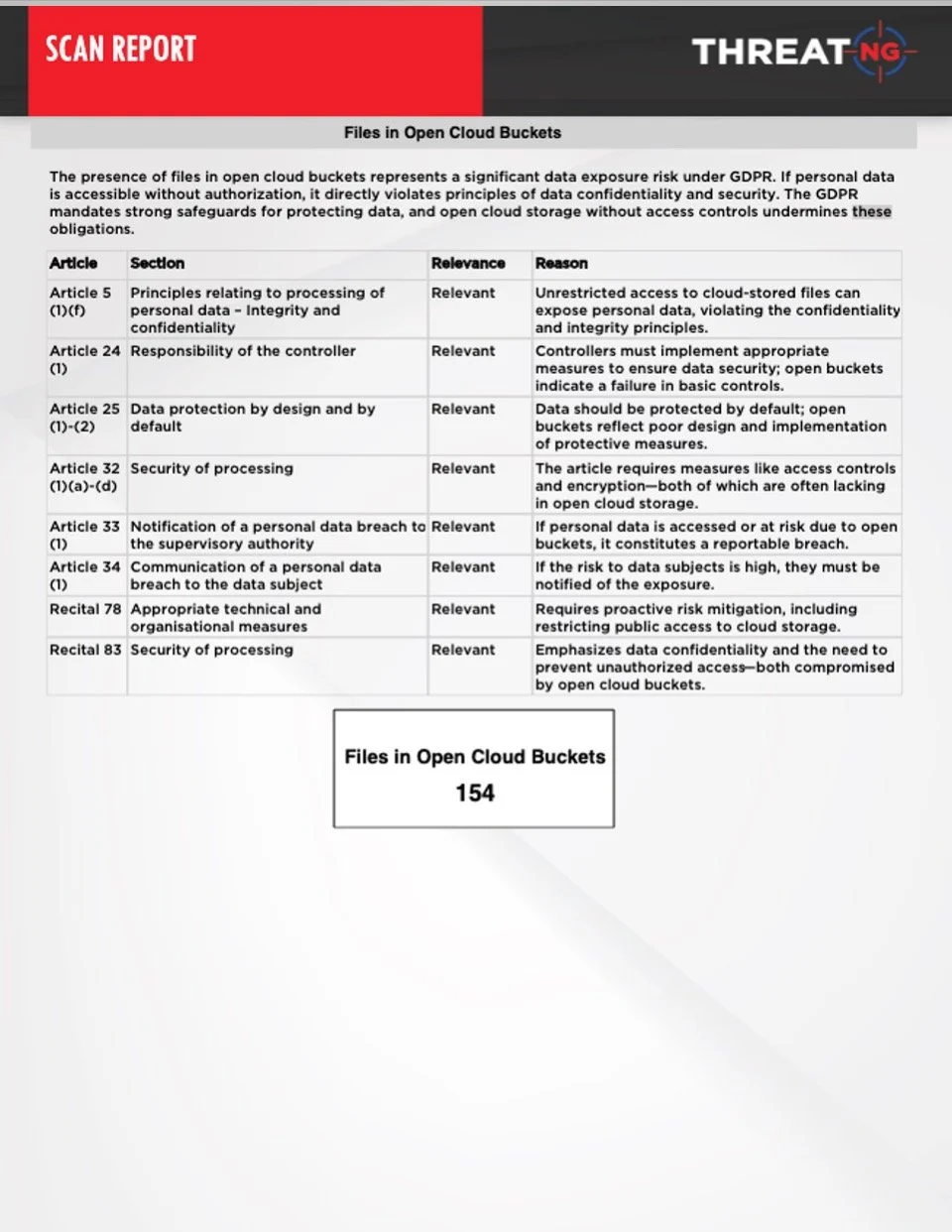
Data Leaks Waiting to Happen
Files in open cloud buckets can expose personal data, a direct violation of GDPR principles, particularly in terms of data confidentiality and security. The presence of APIs on subdomains can expose endpoints that process personal data, creating a risk of unauthorized access.
The Unseen Threat
Unpatched vulnerabilities, a single exposed port, or a publicly accessible developer resource can be the entry point for a ransomware attack. This directly compromises data integrity and availability and could lead to a breach notification and communication to data subjects, per Articles 33 and 34.

The Solution: Get an Attacker's Perspective to Protect Your Data
ThreatNG's External GDPR Assessment gives you an unauthenticated, outside-in evaluation of your entire attack surface. It's a single, continuous monitoring solution that maps what an attacker sees directly to your GDPR compliance framework.
Discover Hidden Vulnerabilities and Stop the Breach Before It Starts: ThreatNG goes beyond traditional scans to discover and prioritize your most critical external security gaps from an attacker's perspective. It identifies vulnerabilities such as subdomain takeovers and sensitive data in open cloud buckets. The solution also identifies exposed APIs and ports that could be used as entry points for an attack. This provides you with the visibility to address risks that could lead to a breach, helping you avoid legal and reputational fallout.
Ensure Continuous Compliance from the Outside In: GDPR is a continuous obligation, not a one-time audit. ThreatNG's continuous monitoring of your external attack surface ensures that as your environment changes, you're always aware of new risks. It aligns your security posture with external threats, mapping findings directly to GDPR articles. For example, the discovery of missing security headers on a subdomain directly relates to Article 32 on "Security of processing". This helps you demonstrate continuous compliance and due diligence.
Move Beyond "What's Broken" to "What's Strong": ThreatNG doesn't just show you your weaknesses; it highlights your strengths. The Positive Security Indicators feature validates your existing security controls from an external perspective. This gives you objective proof of the effectiveness of your security investments and provides a balanced view of your security posture. This builds confidence in your security program and enables you to communicate your team's success to senior leadership more effectively.
Clear GDPR Alignment Through Actionable External Assessments
ThreatNG streamlines your external GDPR assessment by providing clear, actionable insights into your security posture from an attacker's perspective. Our easy-to-read reports detail crucial findings, including personal data exposed in public repositories, compromised credentials, default port scans, and mentions on the dark web. Each finding is meticulously mapped to relevant GDPR articles and principles, enabling organizations to understand their compliance status and prioritize remediation efforts to enhance their security defenses and protect personal data.

Your GDPR Audit Is Done. Your Biggest Threat Is Just Beginning.
Eliminate the "GDPR Audit Blind Spot": Your internal tools can't see exposed cloud buckets with sensitive data, forgotten dev environments with weak credentials, or forgotten subdomains vulnerable to takeover. Our solution operates from an attacker's perspective, using a purely "outside-in" and "unauthenticated" approach to find these exact threats. We empower you to find and fix what others can’t, providing a profound sense of relief from the fear of the unknown.
Move Beyond "Check-the-Box" Compliance: The ultimate goal isn't a clean audit report; it's genuine, demonstrable security that protects your organization from financial and reputational ruin. We don't just find vulnerabilities; we map them directly to the specific GDPR articles they violate, such as Article 5(1)(f) on data integrity and Article 32 on security of processing. This gives you the objective, business-critical data you need to secure buy-in and demonstrate accountability to your board and to regulators.
Become the Proactive Hero: A reactive CISO waits for a breach, an SEC filing, or a lawsuit before taking action. A proactive CISO uses our continuous monitoring capability to get ahead of the threats. We help you detect risks like compromised credentials and ransomware susceptibility before they escalate into a crisis. This capability gives you a constant, real-time pulse on your external risk posture, allowing you to walk into any boardroom with the confidence that you are not just compliant, but truly secure.
Frequently Asked Questions: ThreatNG External GDPR Assessment
In a world where digital threats are constantly evolving, protecting personal data is a top priority—and a legal mandate. You have questions about how to safeguard your organization from an external breach and maintain GDPR compliance. We have answers. Below, we address the most common inquiries to help you understand why an 'outside-in' assessment is a critical component of your security strategy, how it works, and how it empowers you to demonstrate a proactive, modern approach to data protection.
-
Internal audits and traditional penetration tests provide a snapshot of your security from the inside. They are crucial for assessing your internal network and controlled assets. However, they are fundamentally unable to see your organization as an unauthenticated external attacker does. Our assessment solves the "outside-in" blind spot that exists in every enterprise. We identify risks from the public-facing internet, such as forgotten subdomains, exposed developer resources, or data in open cloud buckets—vulnerabilities that an internal scan would miss but that an attacker would find with ease. A clean internal report doesn't protect you from an external threat.
-
The ThreatNG External GDPR Assessment provides a continuous, automated evaluation of your public-facing attack surface. It works by performing "purely external unauthenticated discovery" to identify exposed assets and critical vulnerabilities in the same way an attacker would, without needing any internal access or connectors. The solution then maps these findings directly to the specific GDPR articles they violate, such as data integrity (Article 5) or security of processing (Article 32). We provide a clear, auditable trail that connects technical risks to your legal and financial obligations.
-
Our platform uncovers a wide range of external vulnerabilities that directly relate to GDPR compliance. These include risks from unmanaged assets, such as unmonitored subdomains vulnerable to takeover, misconfigured APIs, or exposed files in open cloud buckets that could leak personal data. It also identifies the presence of compromised credentials on the dark web and pinpoints phishing vulnerabilities related to domain name permutations. Each finding is presented with a clear explanation of how an attacker could exploit it.
-
The GDPR places a heavy burden on the "controller" to not only implement appropriate security measures but also to be able to demonstrate that they have done so. Our continuous assessment provides the concrete, real-time evidence needed to fulfill this obligation. When the platform discovers and helps you remediate a vulnerability, it creates a documented record of your proactive security posture. This allows you to show auditors and regulators that you are actively managing your external risks, thereby supporting your overall Governance, Risk, and Compliance (GRC) standing.
-
Unlike traditional solutions that often rely on internal data and are focused on a single point in time, our approach is built on an "unauthenticated, outside-in" methodology. This means we align your security posture with real-world threats by mimicking the exact discovery process of an adversary. We also go beyond just listing vulnerabilities. Our reports include an embedded knowledge base that provides risk levels, reasoning, recommendations, and reference links to help your team prioritize and take action. This "Us vs. Them" approach empowers you to think and act like an attacker to protect your organization.
-
The assessment provides a prioritized report that categorizes findings by severity: High, Medium, Low, and Informational. This allows you to allocate your resources effectively and focus on the most critical risks that pose the greatest threat to your data and compliance. The knowledge base embedded in the reports provides a deeper understanding of each finding and offers actionable recommendations for remediation.