External NIST CSF Assessment
Governance Oversight Failure: End the Fiduciary Crisis with Continuous, Auditable External NIST CSF Validation
Your current security posture, built on internal VAPT (Vulnerability Assessment and Penetration Testing) and periodic internal audits, gives you a necessary but incomplete illusion of control. Once you look outward, that visibility diminishes. The External National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) Assessment is a strategic solution designed to prevent governance oversight failures by providing objective, continuous validation of your entire attack surface, from exposed VPNs to compromised credentials, against the NIST CSF's five functions. We empower the CISO to transition from guesswork to audit-ready certainty and proactive control.
Strategic Control and Auditable Proof

Achieve Fiduciary Certainty: Prove Due Diligence Against NIST ID.GV-1
You need auditable proof of fiduciary due diligence that satisfies modern risk and oversight mandates. This capability automatically translates every external security flaw, such as exposed Code Secrets Found or Missing HSTS Headers, into a quantifiable NIST control failure (e.g., PR.DS-5, PR.IP-1). This automated mapping eliminates GRC Sprawl and provides continuous, transparent evidence of proactive risk governance (ID.GV-1, ID.RM-1) to address legal, board, and investor scrutiny confidently.
Vanish the External Blind Spot: See What the Adversary Sees (ID.AM-1)
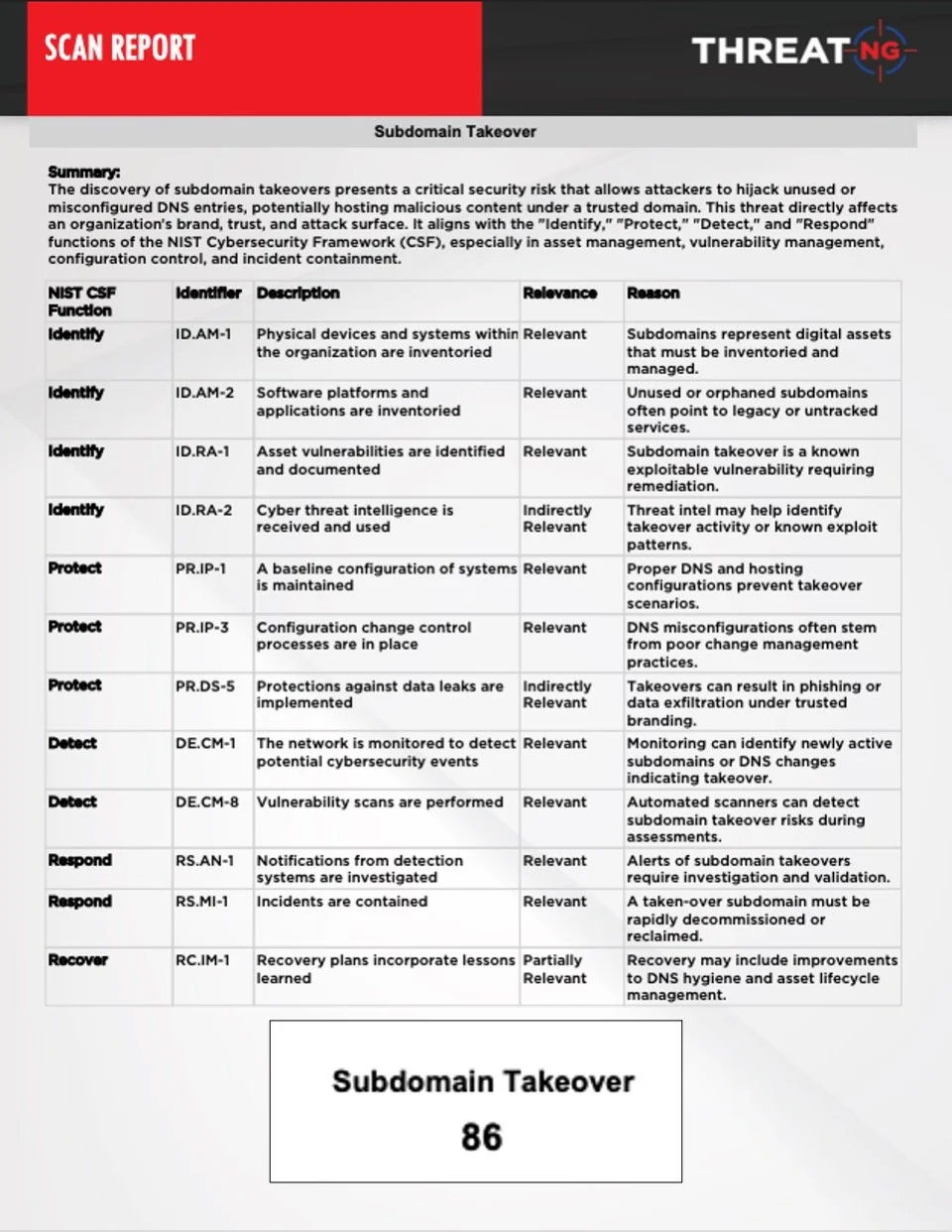
The most significant risk lies in the assets you don't know you own. Our solution performs purely Unauthenticated External Discovery, requiring no connectors, thus removing the internal bias. This process relentlessly maps every externally visible asset from forgotten subdomains and APIs on Subdomains to exposed Files in Open Cloud Buckets. By validating your External Attack Surface Management from the attacker's perspective, we ensure you maintain a complete, up-to-date inventory (ID.AM-1) and secure configuration baseline (PR.IP-1) across your entire digital footprint.

Transition to Continuous, Threat-Driven Validation (ID.RA-5)
Stop wasting time patching low-likelihood risks. Unlike periodic audits, our continuous monitoring validates your posture daily and prioritizes remediation based on real-world exploitability (ID.RA-5). We integrate Known Exploited Vulnerabilities (KEV) and EPSS data to ensure critical failures, such as a vulnerability on an Exposed RDP Port (PR.AC-3), are addressed first. This focused, threat-centric approach transforms vulnerability management (PR.IP-12) from an overwhelmed effort into rapid containment (RS.MI-1), securing your organization against the most immediate, proven threats.
Stop GRC Sprawl: Instant Executive Translation of External Risk to NIST CSF Compliance
The greatest obstacle to achieving strategic security is not finding risks, but manually translating them from technical noise into board-ready compliance language. The External NIST CSF Assessment report eliminates this manual translation effort—known as GRC Sprawl—by providing a continuous mapping of every external finding (such as exposed Open Cloud Buckets or Subdomain Takeover susceptibility) directly to the NIST CSF’s five core functions and relevant subcategories. This core reporting function delivers the objective, auditable proof your governance team needs, allowing you to confidently prove due diligence (ID.GV-1) without ever manually correlating a perimeter vulnerability to a control requirement.
Frequently Asked Questions (FAQ): External NIST CSF Assessment
This FAQ is designed for Chief Information Security Officers (CISOs) and the VP of Risk & Compliance at publicly traded enterprises, focusing on the strategic and fiduciary value of continuous external risk validation.
The Strategic Mandate: Why This is a Necessity
-
Internal vulnerability assessments and penetration testing (VAPT) provide a snapshot of your security from the inside, often relying on authenticated credentials and known assets. This creates an "Illusion of Internal Control." The External NIST CSF Assessment is necessary because modern adversaries attack from the outside in, exploiting assets you didn't even know existed.
It addresses critical NIST failures that internal scans miss:
Asset Inventory Gaps (ID.AM-1): Internal teams often miss exposed VPN endpoints, forgotten cloud resources, or orphaned subdomains.
Configuration Gaps (PR.IP-1): External configuration failures, such as missing basic security headers (HSTS, CSP), are direct violations of secure baselines but are often overlooked by internal tools.
This capability provides the continuous, external assessment required to validate every component of your attack surface from the unauthenticated viewpoint of the adversary.
-
The SEC mandates transparency regarding cybersecurity risk management and oversight (ID.GV-1), making continuous due diligence a fiduciary necessity. A breach originating from an easily discoverable external vulnerability (like exposed Code Secrets or an Open Cloud Bucket) can lead to a public 8-K filing and accusations of negligence.
This capability provides auditable proof of proactive external risk management. It continuously maps critical external risks directly to NIST CSF controls, allowing the CISO to:
Quantify Risk (ID.RA-5): Demonstrate that risk prioritization is based on external likelihood (KEV/EPSS data).
Validate Controls: Provide evidence that controls against data leakage (PR.DS-5) and remote access (PR.AC-3) are continuously effective from the perimeter.
Ensure Regulatory Readiness: Transform reactive compliance into a proactive, documented governance process (ID.GV-1).
-
We focus on external intelligence indicators that precede a successful attack:
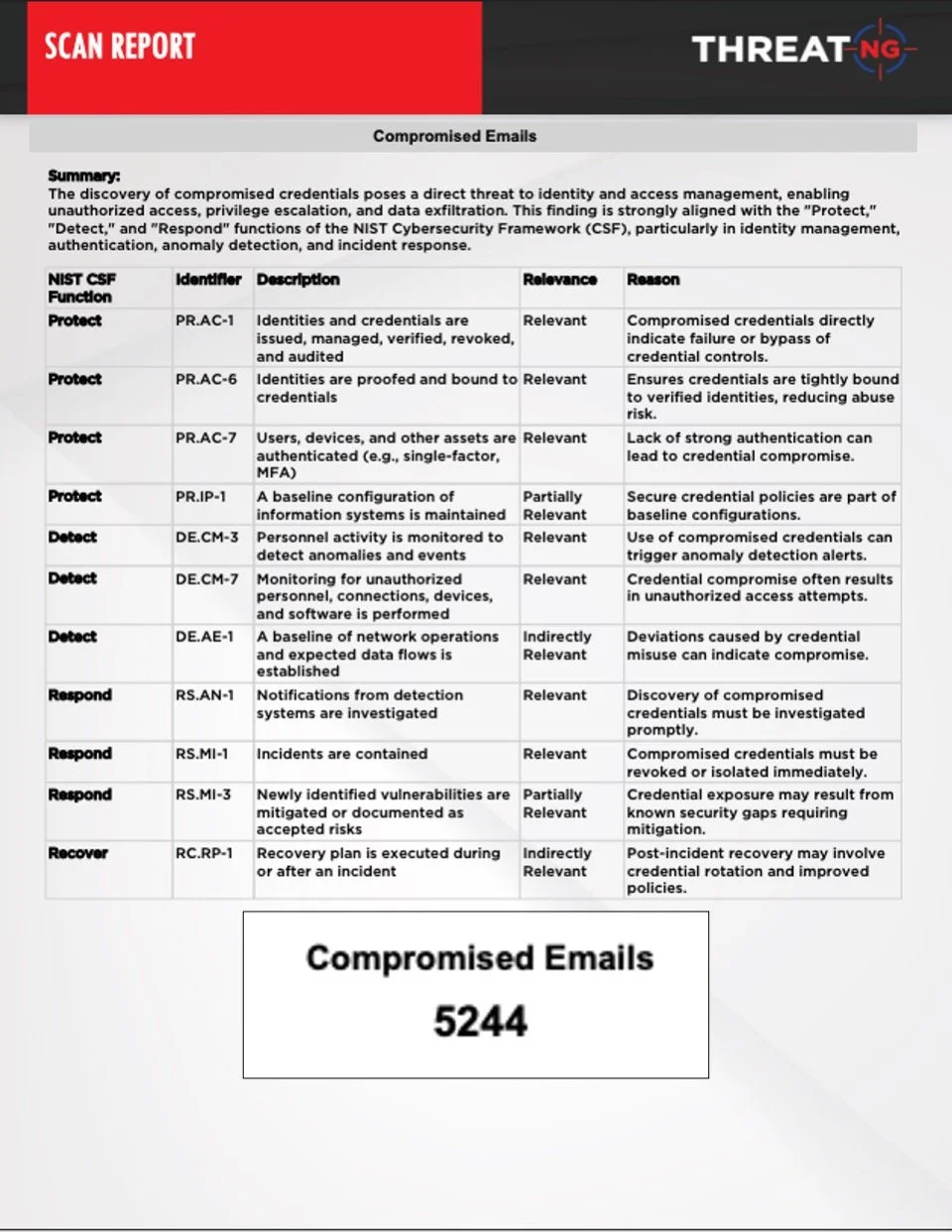
BEC & Phishing: We continuously monitor for Domain Name Permutations - Taken with Mail Record. This is a high-risk indicator that a lookalike domain is actively configured for email spoofing. The platform alerts you to this failure of PR.AC-6 (Identities are proofed) and enables immediate containment (RS.MI-1).
Ransomware: The platform utilizes DarCache intelligence, which includes Known Exploited Vulnerabilities (KEV) and tracks 70+ Ransomware Gangs. Suppose we identify a critical vulnerability on an exposed RDP/SSH port (PR.AC-3 risk) that is listed in KEV. In that case, it receives immediate critical priority, ensuring resources address the most immediate, proven threat (ID.RA-5).
Capability & Function: What Is the Assessment?
-
The External NIST CSF Assessment is a continuous external audit that leverages External Attack Surface Management (EASM) and Digital Risk Protection (DRP) capabilities to measure your organization's external security effectiveness against the five core functions of the NIST CSF (Identify, Protect, Detect, Respond, Recover).
Discovery: It performs purely unauthenticated discovery, mapping every externally visible asset.
Mapping: Every discovered risk—from Compromised Emails to Subdomain Takeover susceptibility —is automatically mapped to the relevant NIST CSF subcategory (e.g., PR.AC-1, ID.AM-2, PR.DS-5).
Scorecarding: It delivers quantified, prioritized reports (High, Medium, Low) and Security Ratings (A through F) that instantly communicate the status of your NIST controls to executives.
-
The assessment uncovers and validates a broad range of critical external assets and misconfigurations that live outside your firewall, such as the following high-risk examples:
Code Secrets Found: Leaked API keys or sensitive information exposed in public code repositories (Violation of PR.DS-1/PR.IP-3).
Open Cloud Buckets: Misconfigured access permissions leading to exposed files in AWS, Azure, or GCP (Violation of PR.DS-5).
Mobile Application Exposure: Sensitive credentials or keys found within decentralized mobile apps.
APIs and Admin Pages: Exposed administrative interfaces or forgotten API endpoints on subdomains that provide an unauthenticated attack vector.
The comprehensive coverage extends to identifying and validating exposures like Subdomain Takeover susceptibility, exposed remote access gateways (VPNs Identified), and unmanaged default network ports (Default Port Scan), ensuring complete external risk visibility.
-
Traditional GRC tools require manual input and mapping of technical findings to compliance frameworks. Standard EASM tools provide inventory and technical alerts.
The External NIST CSF Assessment differentiates itself by integrating three core functions:
Adversary Focus: It performs unauthenticated discovery, showing you exactly how a threat actor sees your perimeter.
Automated GRC Translation: It automatically translates raw technical findings into precise NIST CSF control failures (e.g., Missing HSTS Header = PR.DS-2 Failure) , eliminating the burden on your team.
Threat Prioritization: It uses KEV and EPSS data to prioritize remediation on vulnerabilities that are actively exploited in the wild , satisfying the CISO’s demand for risk-based focus (ID.RA-5).
CISO Value & Outcome: How It Improves Your Life
-
You gain immediate relief from GRC Sprawl. Instead of manually correlating thousands of alerts into board-ready risk language, the External NIST CSF Assessment does it continuously.
This means your team spends less time justifying risks and more time mitigating them. Executive reports are generated automatically, showing performance against NIST functions (Identify, Protect, Detect, Respond, Recover) with clear, prioritized actions (High, Medium, Low). This empowers the CISO to deliver a confident narrative on organizational risk posture to the board, reducing Audit Anxiety and strengthening the role as a strategic leader.
Discovery: It performs purely unauthenticated discovery, mapping every externally visible asset.
Mapping: Every discovered risk—from Compromised Emails to Subdomain Takeover susceptibility —is automatically mapped to the relevant NIST CSF subcategory (e.g., PR.AC-1, ID.AM-2, PR.DS-5).
Scorecarding: It delivers quantified, prioritized reports (High, Medium, Low) and Security Ratings (A through F) that instantly communicate the status of your NIST controls to executives.
-
The ultimate emotional outcome is the transition from perpetual operational stress to quantifiable certainty and control.
Before: You operate with the fear of the unknown external asset, knowing a breach could happen at any moment due to an unmanaged flaw.
After (Shift from Features to Feelings): You gain Control over the attack surface and Confidence in the boardroom. You know that if a high-risk vulnerability exists on your external perimeter, the platform has found it, prioritized it with threat intelligence , and mapped it to a clear NIST control failure (PR.IP-12). This allows you to achieve the peace of mind that comes with proven, auditable due diligence.