External POPIA Assessment
POPIA Compliance: Unmasking Hidden External Risks with ThreatNG
South Africa's Protection of Personal Information Act (POPIA) isn't just a legal checkbox; it's a fundamental mandate for safeguarding personal data. As a "responsible party," your organization faces stringent obligations to protect sensitive information, identify foreseeable risks, and demonstrate continuous accountability. However, in today's complex digital landscape, are you truly aware of all the risks?
The Harsh Realities of Non-Compliance
Massive Fines
Non-compliance with POPIA can result in administrative fines of up to R10 million.
Reputational Damage
Data breaches erode customer trust, damage your brand, and can have long-lasting negative impacts on your market standing.
Legal Liabilities
Affected individuals can pursue civil claims for damages, leading to costly litigation.
Operational Disruption
Security incidents divert critical resources, impacting business continuity and productivity.
The Hidden Problem: Your Blind Spots to External Risks
POPIA explicitly requires you to identify "all reasonably foreseeable internal and external risks to personal information" [Section 19(2)(b)]. Yet, traditional security tools often focus internally, leaving vast portions of your external digital footprint—what an attacker sees—unmonitored. This includes:
Forgotten Assets
Old subdomains, archived web pages, or misconfigured cloud services you're unaware of.
Shadow IT
Unsanctioned applications or services deployed without security oversight.
Third-Party Exposures
Vulnerabilities are introduced through your vendors and supply chain.
Accidental Leaks
Sensitive code, credentials, or private IPs exposed in public repositories or misconfigurations.

ThreatNG: Your Proactive POPIA Compliance Partner
ThreatNG is an all-in-one External Attack Surface Management (EASM), Digital Risk Protection (DRP), and Security Ratings solution designed to give you the crucial "attacker's view" of your digital footprint. We empower you to identify and mitigate external risks proactively, ensuring demonstrable POPIA compliance and fortifying your overall security posture.
Our Promise: Unparalleled External Visibility & Proactive Protection
ThreatNG directly addresses POPIA's core requirements by continuously monitoring your external attack surface, identifying vulnerabilities and exposures before they can be exploited.
POPIA Challenge: Preventing Data Leaks & Unauthorized Exposure
POPIA Requirements and ThreatNG Solutions
-
ThreatNG Solution - Files in Open Cloud Buckets: Identifies publicly exposed AWS, Azure, and GCP buckets.
-
ThreatNG Solution - Code Secrets Found: Discovers exposed API keys, access tokens, and cryptographic keys in public code repositories.
-
ThreatNG Solution - Code Secrets Found: Discovers exposed API keys, access tokens, and cryptographic keys in public code repositories.
-
ThreatNG Solution - Mobile Application Exposure Sensitive Information Found: Evaluates mobile apps for exposed access/security credentials.
-
Archived Web Pages: Finds old web pages containing sensitive data like emails, usernames, or documents.
-
Private IPs Found: Identifies internal IP addresses exposed publicly.
POPIA Challenge: Mitigating Attack Surface Vulnerabilities & Misconfigurations
POPIA Requirements and ThreatNG Solutions
-
ThreatNG Solution - Subdomain Takeover Susceptibility: Assesses the risk of malicious actors taking control of your subdomains.
-
ThreatNG Solution - Missing Security Headers (CSP, HSTS, X-Content-Type, X-Frame-Options, Referrer-Policy): Identifies critical web security misconfigurations.
-
ThreatNG Solution - Invalid Certificates: Flags issues with TLS/SSL certificates that undermine encryption.
-
ThreatNG Solution - Default/Custom Port Scans: Discovers open and exposed ports that serve as entry points for attackers.
-
ThreatNG Solution - APIs on Subdomains: Identifies exposed APIs that handle personal information exchanges.
-
ThreatNG Solution - Applications & Admin Pages: Highlights critical login pages and administrative panels.
-
ThreatNG Solution - Critical/High Vulnerabilities Found: Identifies unpatched vulnerabilities with real-world exploitability (NVD, EPSS, KEV, PoC Exploits).
POPIA Challenge: Combating Brand Impersonation & Phishing
POPIA Requirements and ThreatNG Solutions
-
ThreatNG Solution - Domain Name Permutations - Taken with Mail Record: Detects lookalike domains used for phishing campaigns.
-
ThreatNG Solution - Dark Web Mentions: Uncover discussions of your organization's data or brand on the dark web.
POPIA Challenge: Enhancing Incident & Risk Management Posture
POPIA Requirements and ThreatNG Solutions
-
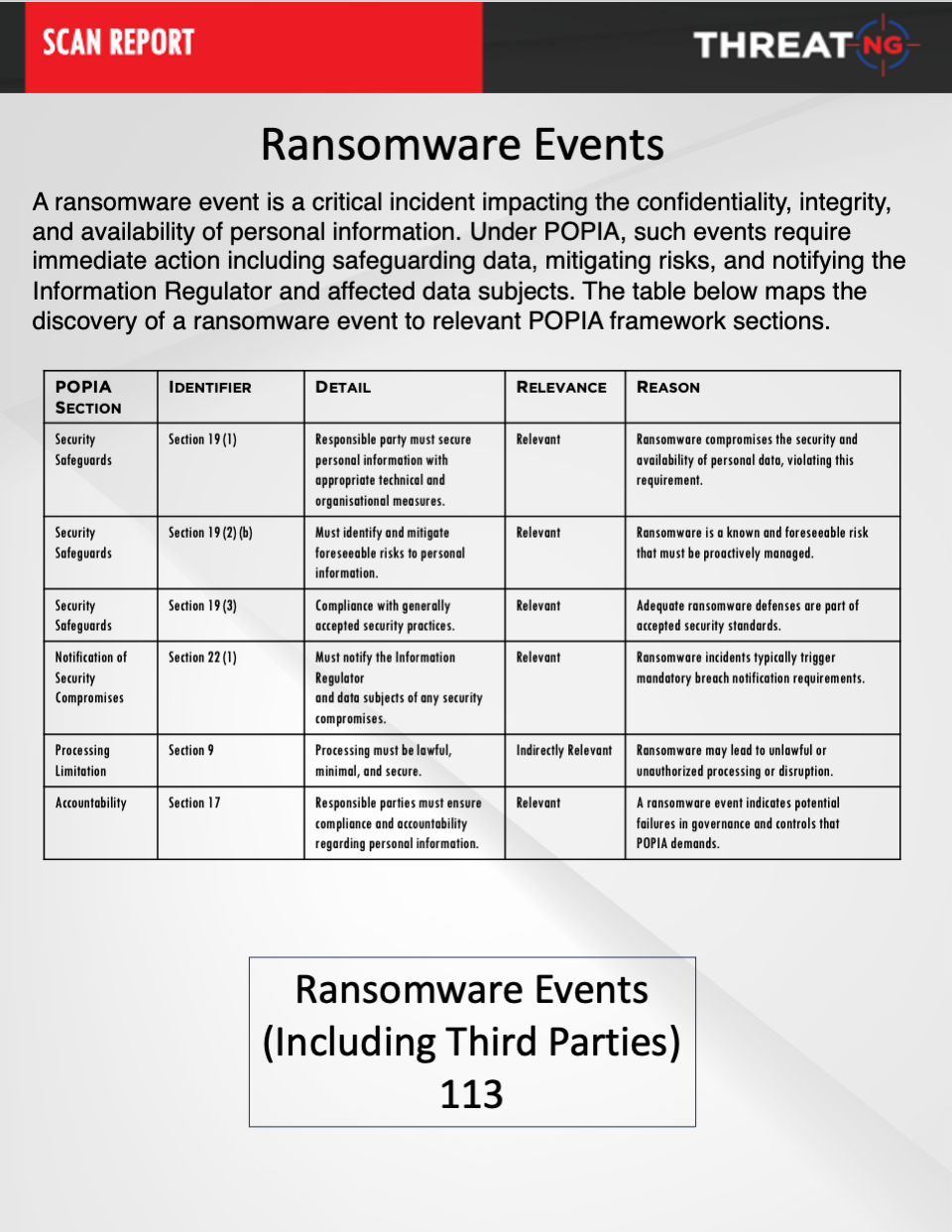
ThreatNG Solution - Ransomware Events: Tracks ransomware groups and activities relevant to your organization.
-
ThreatNG Solution - 8K Security Incident Filings: Monitors public disclosures of security incidents (for publicly traded companies).
-
ThreatNG Solution - WAF Presence/Absence: Verifies the presence and effectiveness of Web Application Firewalls.
-
ThreatNG Solution - Bug Bounty and Responsible Disclosure Presence: Highlights proactive security engagement.
Mapping External Threats to POPIA Compliance for Enhanced Data Protection
ThreatNG offers clear, actionable insights into an organization's POPIA compliance posture through its External POPIA Assessment. The platform provides easy-to-read reports that map specific external findings, such as missing content security policies, open cloud buckets, or exposed admin pages, directly to relevant sections of the POPIA framework. These reports detail the implications and reasons for their relevance to security safeguards, accountability, and the lawful processing of personal information. This allows organizations to understand how identified vulnerabilities and exposures align with their obligations under POPIA, facilitating targeted remediation and continuous compliance efforts.

What Makes ThreatNG Different? The Unfair Advantage.
In a world of fragmented security solutions, ThreatNG stands apart by offering a truly comprehensive and proactive approach to POPIA compliance:
Purely External, Unauthenticated Discovery: Unlike internal scans or periodic penetration tests, ThreatNG operates entirely from an attacker's perspective, without requiring any internal access or connectors. This is critical for identifying the "unknown unknowns" and "foreseeable external risks" that POPIA mandates you address [Section 19(2)(b)].
Continuous Monitoring, Not Point-in-Time Snapshots: Your external attack surface is constantly evolving. ThreatNG provides continuous, real-time monitoring of your digital footprint, ensuring you're always aware of new exposures and vulnerabilities as they emerge. This directly supports POPIA's requirement for security measures to be "updated in response to new risks" [Section 19(2)(c)].
Actionable Intelligence & Prioritization: We don't just tell you what's wrong; we tell you how to fix it. ThreatNG's Knowledgebase provides clear "Reasoning," "Recommendations," and "Reference links" for every identified risk, enabling your teams to prioritize and effectively remediate the most critical threats. Our integration of NVD, EPSS, KEV, and Verified Proof-of-Concept Exploits lets you focus on vulnerabilities that are not only severe but also actively being exploited in the wild.
All-in-One Solution: ThreatNG consolidates External Attack Surface Management, Digital Risk Protection, and Security Ratings into a single, intuitive platform. This eliminates tool sprawl, streamlines workflows, and provides a holistic view of your external security posture, making POPIA compliance management more straightforward and more efficient.
Demonstrable Accountability: Our "External GRC Assessment" continuously evaluates your GRC posture from an external viewpoint, mapping findings directly to relevant frameworks. This provides objective, auditable evidence of your "appropriate, reasonable technical and organisational measures" (POPIA Section 19(1)), empowering your Information Officer and executive leadership to demonstrate due diligence and accountability (POPIA Section 17).
Ready to Transform Your POPIA Compliance?
Don't let hidden external risks jeopardize your POPIA compliance and expose your organization to severe consequences. With ThreatNG, you gain the clarity, control, and confidence needed to protect personal information and build lasting digital trust proactively.
Take the first step towards a truly secure and compliant future.
Request a Demo: See ThreatNG's capabilities in action and how they map directly to your organization's unique external risks.
Get Free Evaluation Access: Experience firsthand what an attacker sees. Discover your hidden exposures and receive a preliminary report on your POPIA-relevant external risks.
Contact Us Today: Our experts are ready to discuss your specific POPIA compliance challenges and tailor a solution that fits your needs.
ThreatNG: See What Attackers See. Stay POPIA Compliant. Stay Secure.
Frequently Asked Questions
This FAQ addresses common questions about ThreatNG Security's role in enhancing POPIA compliance, highlighting its unique external perspective and continuous monitoring capabilities.
-
Before solutions like ThreatNG Security, organizations often relied heavily on internal audits, penetration tests, and manual assessments, which provided only a snapshot of their security posture at a given point in time. Demonstrating compliance with POPIA, especially concerning external risks, was challenging because:
Blind Spots: Organizations struggled to identify all their external digital assets and the vulnerabilities visible from an attacker's perspective.
Reactive Security: Compliance efforts were often reactive, addressing issues after they had been exploited or identified through time-consuming manual processes.
Lack of Continuous Visibility: It was challenging to maintain an up-to-date understanding of the ever-changing external threat landscape and how new exposures impacted POPIA obligations.
Subjective Risk Assessment: Assessing "foreseeable external risks" (POPIA Section 19(2)(b)) lacked objective, continuous data from the outside-in.
Disjointed Compliance Evidence: Linking technical security findings directly to specific POPIA sections for audit and accountability was often a manual and complex task.
-
POPIA, the Protection of Personal Information Act 4 of 2013, is South Africa's comprehensive data privacy law. It governs the lawful processing of personal information, upholding the constitutional right to privacy. Its significance lies in its strict regulations on how organizations collect, use, store, and disclose personal information, with severe penalties for non-compliance, including administrative fines up to R10 million, imprisonment, and significant reputational damage. It mandates a proactive approach to data protection.
-
POPIA affects any natural or juristic person (individual or legal entity) that processes personal information within South Africa, regardless of where they are located. Compliance is essential for:
Responsible Parties: Organizations that determine the purpose and means of processing personal information, holding the primary legal responsibility.
Information Officers: Legally designated to oversee POPIA compliance, data governance, and incident response.
CISOs and Security Leadership: Tasked with implementing robust technical safeguards and managing cybersecurity risks that impact personal information.
Legal and Compliance Teams: Focused on ensuring regulatory adherence, drafting policies, and minimizing legal exposure.
Risk Management Teams: Responsible for identifying, assessing, and mitigating enterprise-wide risks, including those related to data privacy and security.
Executive Leadership and Boards: Ultimately accountable for the organization's compliance, reputation, and financial well-being.
-
POPIA compliance is critically important for several reasons:
Legal and Financial Protection: It helps organizations avoid substantial fines and potential legal action arising from data breaches or non-compliance.
Reputation and Trust: Demonstrating strong data protection practices fosters and maintains customer trust, safeguarding the organization's reputation in an increasingly privacy-aware world.
Ethical Responsibility: It reflects an organization's commitment to respecting individuals' rights to privacy.
Operational Resilience: Robust security measures mandated by POPIA enhance an organization's ability to prevent, detect, and respond to cyber threats, ensuring business continuity.
Competitive Advantage: A Strong privacy posture can differentiate an organization in the market.
-
ThreatNG's approach is uniquely differentiated by its purely external, unauthenticated discovery capability. This means it continuously scans your digital footprint from an attacker's perspective, without requiring any internal access or connections. This "outside-in" view identifies vulnerabilities and exposures—such as open cloud buckets, exposed APIs, or compromised credentials on the dark web—that are often overlooked by internal tools.
The core of ThreatNG's differentiation for POPIA is its explicit mapping of every discovery and assessment finding directly to relevant POPIA sections and conditions. This is a powerful proof point for compliance, as it means:
Clear Accountability: When ThreatNG identifies an "Invalid Certificate" (a technical finding), it directly explains its Direct Relevance to POPIA Section 19(1) ("securing personal information") and 19(2)(b) ("identifying foreseeable risks"), as it weakens encryption and data security. This clear link enables Information Officers to demonstrate that "appropriate, reasonable technical and organisational measures" are being taken (Section 19(1)).
Actionable Compliance: Organizations no longer have to interpret how a technical vulnerability impacts their legal obligations manually. ThreatNG provides this crucial context. For instance, detecting "Files in Open Cloud Buckets" is mapped as Relevant to POPIA Section 19(1) (failure to secure confidentiality) and Section 22(1) (potential breach notification), guiding immediate action.
Evidence for Audits: This direct mapping provides auditable evidence, streamlining compliance reporting and external assessments. It helps articulate precisely how ThreatNG identifies and mitigates risks that fall under POPIA's specific requirements.
This continuous, outside-in evaluation with direct POPIA mapping ensures organizations actively address and demonstrate compliance with POPIA's mandate to identify "all reasonably foreseeable internal and external risks" and to adapt security measures in response to new threats (Section 19(2)(b), 19(2)(c)).
-
ThreatNG directly solves critical POPIA challenges by proactively identifying external risks that can lead to non-compliance, particularly concerning Section 19 (Security Safeguards) and Section 22 (Notification of Security Compromises). Key problems solved include:
Uncovering Data Leaks & Unauthorized Exposure:
Files in Open Cloud Buckets: ThreatNG identifies publicly accessible storage buckets (AWS, Azure, GCP), which are Relevant to POPIA Section 19(1) (securing confidentiality) and 19(2)(b) (foreseeable risks). If personal data is found, it's Relevant to Section 22(1) (breach notification).
Compromised Credentials: Monitoring the Dark Web for stolen employee/customer login details is Relevant to POPIA Section 19(1) (security of personal information) and Section 22(1) (mandatory breach notification).
Exposed Code Secrets: Discovering API keys, tokens, and cryptographic keys in public code repositories is Relevant to POPIA Section 19 (Security Safeguards) and Section 22 (Breach Notification), indicating a failure in data protection.
Sensitive Information in Mobile Apps: Evaluating mobile applications for exposed credentials or personal data is Relevant to POPIA Section 19 (Security Safeguards) and Section 22 (Breach Notification).
Mitigating Attack Surface Vulnerabilities & Misconfigurations:
Subdomain Takeover Susceptibility: Identifies the risk of malicious control over subdomains, which is Relevant to POPIA Section 19(1) (securing personal information) and 19(2)(b) (foreseeable risks), as it enables impersonation and data compromise.
Missing Security Headers: Flags critical web security misconfigurations (e.g., missing CSP, HSTS), Relevant to POPIA Section 19 (Security Safeguards) for preventing client-side attacks and data compromise.
Exposed Services/Ports & APIs: Discovers publicly exposed network services, applications, and APIs, which are Relevant to POPIA Section 19 (Security Safeguards) and 19(2)(b) (foreseeable risks), as they serve as potential attack entry points.
High-Severity Vulnerabilities: Identifies unpatched critical vulnerabilities with known exploits, Relevant to POPIA Section 19(1) (securing personal information) and 19(2)(b) (foreseeable risks), ensuring proactive remediation of exploitable weaknesses.
Combating Brand Impersonation & Phishing:
Lookalike Domains (Phishing): Detects domain permutations used for phishing, Relevant to POPIA Section 19(1) (securing personal information) and 19(2)(b) (foreseeable risks), as these can deceive data subjects and lead to data compromise.
Dark Web Mentions: Alerts to discussions of your organization's data or brand on the dark web, Relevant to POPIA Section 19(1) (security safeguards) and Section 22(1) (notification of security compromises).
-
Item descriThreatNG significantly enhances existing POPIA compliance frameworks and security solutions:
Augments Internal Security Tools: While internal vulnerability scans and penetration tests are vital, ThreatNG provides the crucial external perspective, identifying risks only visible from an attacker's viewpoint. This directly helps fulfill the mandate of POPIA Section 19(2)(b) to identify external, foreseeable risks.
Empowers Legal and GRC Teams: Consulting firms specializing in POPIA compliance (e.g., legal advisory, policy development, PIIAs) can leverage ThreatNG's precise, mapped technical findings to provide more comprehensive, objective, and evidence-based assessments of their clients' external security posture, offering a more robust and auditable compliance solution.
Strengthens Managed Security Services: For MSSPs, ThreatNG's continuous external monitoring provides an invaluable layer of defense and real-time risk visibility, perfectly complementing their existing detection and response capabilities.
Validates Security Controls: ThreatNG can continuously verify the external effectiveness of implemented security controls, such as Web Application Firewalls (WAFs) or secure network configurations, ensuring they effectively protect personal information as required by POPIA Section 19.
Supports Robust Third-Party Risk Management: Through its "Supply Chain & Third Party Exposure" capability, ThreatNG provides objective, continuous security ratings of vendors. This moves beyond questionnaire-based assessments to ensure that third-party operators adhere to POPIA's security requirements (Section 19, Section 17), mitigating risks from your supply chain.
By integrating ThreatNG, organizations can achieve a more holistic, proactive, and demonstrably compliant POPIA posture, effectively bridging the gap between internal security efforts and the dynamic external threat landscape.