PCI DSS and The Supply Chain: Unmasking Your Extended Risk with ThreatNG
The traditional idea of a secure "perimeter" around an organization's network is becoming increasingly outdated. Cyber threats have advanced, often targeting the weakest points within an organization's extended supply chain. This fundamental shift necessitates a broader security approach that extends well beyond an organization's immediate digital boundaries.
At the core of safeguarding sensitive financial information is the Payment Card Industry Data Security Standard (PCI DSS). This globally recognized security standard, created by the PCI Security Standards Council (PCI SSC), seeks to prevent payment card fraud by requiring organizations that process, store, or transmit credit card data to maintain secure systems. Compliance with the PCI DSS is mandatory for all entities involved in payment card processing, regardless of their size or transaction volume, as mandated by major credit card brands, including Visa, MasterCard, American Express, Discover, and JCB.
Achieving and maintaining PCI DSS compliance is no longer just an internal effort. It fundamentally requires strong management of risks from third-party (direct vendors) and Nth-party (vendors of vendors) relationships, which often create major compliance blind spots. This article will show that the security boundary for cardholder data is no longer limited to an organization's direct network; instead, it extends across the entire ecosystem. This makes 'unmasking your extended risk' not just an engaging title but a strategic necessity for compliance. While PCI DSS offers a vital baseline of technical and operational standards, adequate security demands a comprehensive approach that anticipates risks inherent to interconnected digital operations, even if they are not explicitly outlined in every PCI DSS sub-requirement. ThreatNG offers a detailed and proactive solution to identify and safeguard this complex extended digital ecosystem, ensuring ongoing PCI DSS compliance.
PCI DSS: A Foundation for Cardholder Data Security
Laying the Groundwork: Key Requirements for PCI DSS Compliance
The Payment Card Industry Data Security Standard (PCI DSS) is a unified set of requirements designed to enhance the security of payment account data globally. Developed by the PCI Security Standards Council (PCI SSC), a joint effort of major payment brands including American Express, Discover Financial Services, JCB International, Mastercard Worldwide, and Visa Inc., its primary goal is to promote the widespread adoption of consistent data security practices to combat identity theft and fraud.
The scope of PCI DSS is broad, covering all entities that store, process, or transmit cardholder data (CHD) or sensitive authentication data (SAD), or whose systems could affect the security of the Cardholder Data Environment (CDE). This broad scope encompasses a diverse range of participants in the payment ecosystem, including merchants, payment processors, acquirers, issuers, and various service providers.
Compliance validation requirements for merchants vary based on factors such as their annual transaction volume, the specific payment processing method used, and any previous data breach incidents. Validation can range from annual Self-Assessment Questionnaires (SAQs) for smaller businesses to mandatory onsite yearly audits conducted by a Qualified Security Assessor (QSA) and quarterly network scans performed by an Approved Scanning Vendor (ASV) for larger organizations.
The 12 Core Requirements of PCI DSS
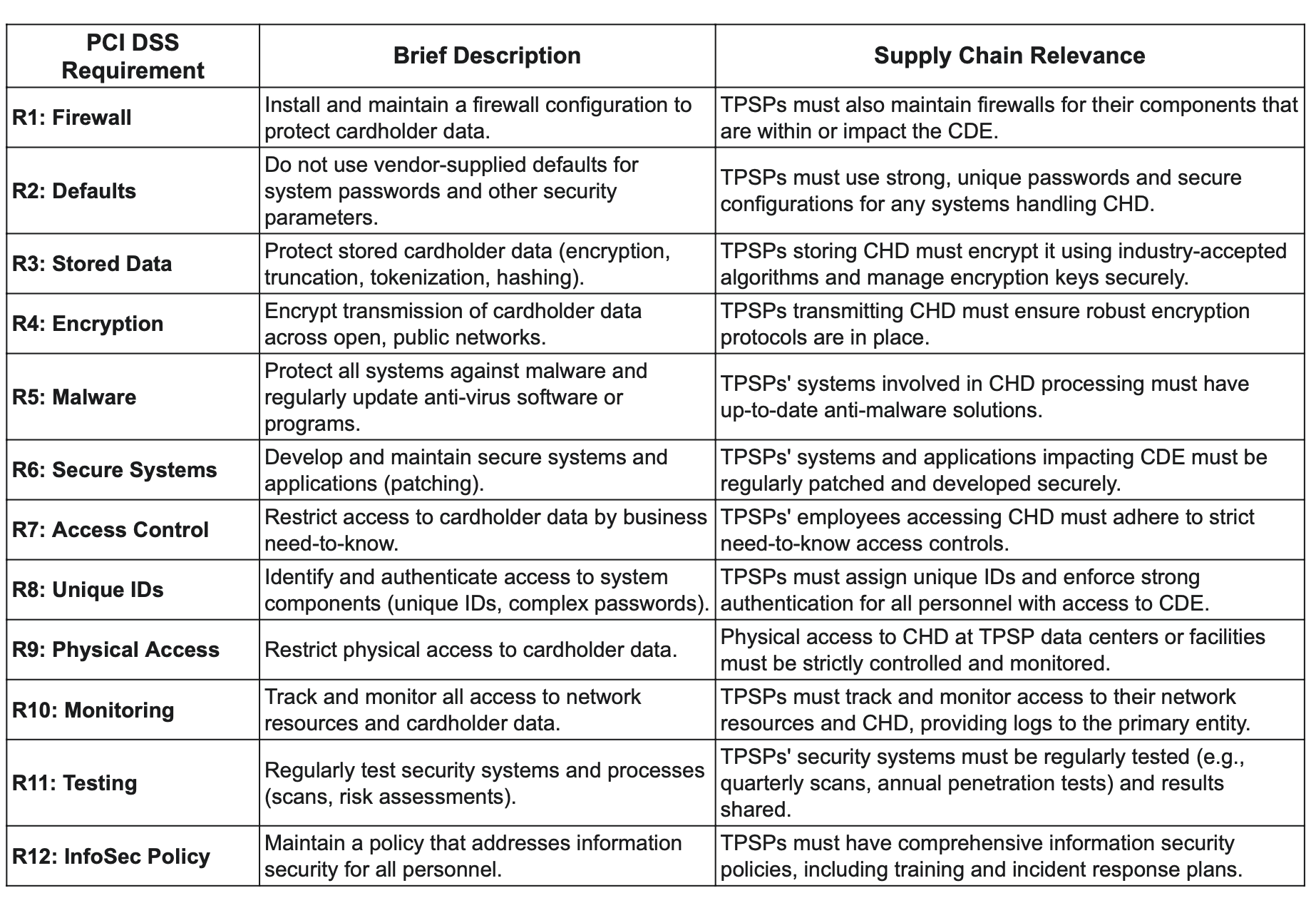
PCI DSS is structured around six overarching control objectives, which are further delineated into 12 core requirements. These requirements establish a robust security framework for safeguarding credit card information. They serve as the fundamental pillars for protecting cardholder data:
Objective 1: Build and Maintain a Secure Network and Systems
Requirement 1: Install and maintain a firewall configuration to protect cardholder data. This involves establishing and documenting firewall and router standards to control access to the network.
Requirement 2: Avoid using vendor-supplied defaults for system passwords and other security parameters. This mandates changing default passwords, removing unnecessary default accounts, and disabling unnecessary services to enhance system security.
Objective 2: Protect Cardholder Data
Requirement 3: Protect stored cardholder data. This necessitates limiting the storage of sensitive data and employing strong cryptographic techniques, such as encryption (e.g., AES-256, RSA 2048), truncation, tokenization, or hashing (e.g., SHA-256). Robust key management procedures are also critical.
Requirement 4: Encrypt transmission of cardholder data across open, public networks. This ensures that data is unreadable and unusable in transit, safeguarding it from interception.
Objective 3: Maintain a Vulnerability Management Program
Requirement 5: Protect all systems against malware and regularly update anti-virus software or programs. Maintaining up-to-date anti-malware programs is essential to prevent infections.
Requirement 6: Develop and maintain secure systems and applications. This includes promptly patching all systems within the card data environment, such as operating systems, firewalls, applications, and POS terminals.
Objective 4: Implement Strong Access Control Measures
Requirement 7: Restrict access to cardholder data based on a business need-to-know. Access control systems must prevent unauthorized individuals from accessing sensitive data.
Requirement 8: Identify and authenticate access to system components. Each authorized user must have a unique ID, and passwords must be adequately complex to ensure accountability.
Requirement 9: Restrict physical access to cardholder data. This involves monitoring entry and exit points with video cameras or electronic access controls, retaining access logs for a minimum of 90 days, and physically protecting all media containing cardholder data.
Objective 5: Regularly Monitor and Test Networks
Requirement 10: Track and monitor all access to network resources and cardholder data. This includes logging and reviewing activities to detect unauthorized access.
Requirement 11: Regularly test security systems and processes. This mandates frequent testing, including quarterly wireless analyzer scans to detect unauthorized wireless access points and an annual formal risk assessment.
Objective 6: Maintain an Information Security Policy
Requirement 12: Maintain a policy that addresses information security for all personnel. This comprehensive policy should cover user awareness training, employee background checks, and robust incident management procedures.
Your Vendor's Risk, Your Compliance Burden: Navigating PCI DSS Third-Party Liabilities
Organizations often outsource various credit card operations to Third-Party Service Providers (TPSPs). These operations can include application hosting, data centers, payment gateway providers, cloud infrastructure, encryption or tokenization services, managed security services, and payment processors. Although outsourcing can improve efficiency, a key aspect of the PCI DSS is that the primary organization remains ultimately responsible for ensuring that the third-party service provider protects cardholder data in accordance with the PCI DSS requirements. Therefore, the security stance of TPSPs directly affects the primary entity's ability to attain and sustain PCI DSS compliance.
The PCI Security Standards Council provides specific guidance for Third-Party Risk Management (TPRM) programs, emphasizing the importance of thorough vendor due diligence, clear connections between services and PCI DSS requirements, and robust written agreements. For example, if a TPSP handles cardholder data—such as a cloud provider storing encrypted data or a payment gateway processing transactions—their compliance with requirements like firewall configurations (Requirement 1), strong passwords (Requirement 2), data encryption (Requirements 3 and 4), vulnerability management (Requirements 5 and 6), and access controls (Requirements 7 and 8) directly impacts the merchant's overall PCI DSS compliance. A vulnerability in a TPSP's system, like unpatched software or weak access controls, can lead to a direct compliance failure for the main organization, highlighting the need for ongoing oversight and verification of all entities that interact with the Cardholder Data Environment.
Additionally, the definition of a "service provider" within PCI DSS can be complex. For instance, an entity that only offers public network access, like a telecommunications company, might not be considered a service provider for that specific function, but it could be for other services. This difference underscores the importance of organizations clearly understanding their vendors' roles and responsibilities. Misclassifying a vendor or underestimating their potential impact on the CDE can cause significant compliance gaps. Therefore, conducting thorough vendor due diligence and creating clear, written agreements that outline responsibilities are essential. A strong TPRM program must be flexible and capable of re-evaluating vendor relationships as services change.
To demonstrate the widespread applicability of PCI DSS requirements throughout the supply chain, the following table links each core requirement to its importance in third-party interactions.
Table: PCI DSS Requirements & Supply Chain Relevance
The Unseen Attack Vectors: Common Challenges in Securing Your Extended Digital Ecosystem
While PCI DSS provides clear guidelines for internal security, the complexities of the digital supply chain often create significant compliance blind spots. Organizations frequently rely on a network of third-party and even Nth-party vendors, each introducing potential vulnerabilities that can compromise cardholder data, even if general supply chain security discussions do not explicitly mention cardholder data.
Common Challenges in Digital Supply Chain Security
The interconnected nature of modern business operations exposes organizations to a wide range of risks arising from their digital supply chains. These challenges include:
Cybersecurity Threats: Manufacturers and their partners continually face various cybersecurity threats, such as malware, ransomware, phishing attacks, and unauthorized access attempts. These malicious activities can result in data breaches, system disruptions, and the theft of sensitive information, including cardholder data.
Third-Party Risks: Working with multiple third-party vendors, suppliers, and partners inherently creates significant vulnerabilities. These external entities may not adhere to the security practices and data handling standards of the primary organization, which could result in data breaches or unauthorized access to cardholder information.
Insider Threats: Both intentional malicious acts and accidental negligence by employees, contractors, or partners within the supply chain pose significant risks. These insider actions can lead to unauthorized data leaks or the misuse of sensitive information. Notable examples, such as the Tesla data leak orchestrated by former employees or the unintentional exposure of login credentials at Microsoft, underscore the real danger that insider threats pose.
Data Governance and Compliance: Managing large amounts of sensitive data, including cardholder information, across multiple stakeholders while ensuring compliance with relevant privacy laws and industry standards is a highly complex task. Failure to comply can result in severe legal penalties and reputational damage.
Supply Chain Visibility and Data Sharing: Ensuring secure data sharing and maintaining adequate visibility of sensitive information across a diverse ecosystem of manufacturers, suppliers, logistics providers, and customers poses a significant challenge. This requires the implementation of secure data exchange protocols, strong encryption techniques, and clearly outlined data-sharing agreements.
Cloud Security: The widespread use of cloud computing services for data storage and processing brings unique security risks. Issues such as data breaches, unauthorized access to cloud accounts, and weak data encryption can occur if cloud environments are not adequately managed and secured by all parties involved in the supply chain.
Data Retention and Disposal: Retaining data longer than necessary significantly increases the risk of data breaches and privacy violations. Creating clear data retention policies and ensuring data is securely and adequately disposed of are essential throughout the entire digital supply chain to prevent unauthorized access to sensitive information in outdated or discarded systems.
Fragmented Collaboration and Lack of Transparency: Beyond these specific technical and operational concerns, common challenges also include fraud, counterfeiting, and a general lack of transparency among supply chain partners, which can further obscure risk.
From Due Diligence to Continuous Monitoring: PCI DSS's Directives for Vendor Security
Recognizing the critical role of external entities, PCI DSS explicitly addresses third-party risk management in sections 12.8 and 12.9. These requirements are designed to ensure the continuous protection of cardholder data when it is shared with or could be impacted by service providers. These are not optional guidelines but mandatory components of compliance
12.8.1: Maintain a list of service providers: Organizations are required to keep an up-to-date and comprehensive list of all service providers, along with a clear description of the specific services they provide. This crucial step enables an organization to identify where potential risks extend beyond its internal boundaries accurately.
12.8.2: Maintain a written agreement: A formal, written agreement must be established with each service provider. This agreement must include an acknowledgment from the service provider that they are responsible for the security of cardholder data they possess, store, process, or transmit on behalf of the customer, or to the extent that their services could impact the Cardholder Data Environment. This ensures a mutual and documented understanding of PCI DSS responsibilities.
12.8.3: Established process for engaging service providers, including due diligence: Organizations must have a documented process for engaging service providers, which includes thorough due diligence conducted before engagement. This vetting process should thoroughly assess the vendor's security practices, breach notification procedures, incident response plans, and validation of their own PCI DSS compliance.
12.8.4: Monitor service providers’ PCI DSS compliance status at least annually: Organizations must maintain a program designed to monitor their service providers’ PCI DSS compliance status on at least an annual basis. This provides ongoing assurance that the third parties are upholding their security obligations. Service providers have options for validation, including conducting their own yearly PCI DSS assessments (and providing evidence such as an Attestation of Compliance (AOC) or a Report on Compliance (ROC)) or participating in on-demand assessments for their customers.
12.8.5: Maintain information about which each party manages PCI DSS requirements: Organizations must maintain clear documentation that explicitly outlines which specific PCI DSS requirements are managed by the service provider and which remain the responsibility of the primary entity. This clarifies shared responsibilities and is vital for preventing compliance gaps.
Beyond Your Vendors: Why Nth-Party Risks Are Your Next PCI DSS Challenge
Beyond direct third-party vendors, the digital supply chain extends into a complex web of interconnected entities, giving rise to "Nth-Party Risk." This term refers to risks originating from entities several levels removed from an organization within its supply chain or broader business ecosystem. This includes, for example, your third-party vendors' vendors (known as fourth parties), and so on, creating a chain of dependencies.
These Nth-party relationships often carry hidden risks. Even if an organization has implemented robust security measures for its direct vendors, it may still have limited visibility into the security practices of its sub-vendors. Attackers can exploit these less visible vulnerabilities to gain unauthorized access to an organization's systems or data, resulting in a ripple effect that can compromise the entire network.
A security incident involving an Nth party, even if it does not directly impact the immediate environment of the primary organization, can still severely harm that organization's reputation and weaken customer trust. Managing Nth-party risk is challenging because it requires a thorough understanding of the entire supply chain and business ecosystem, including the complex relationships between different entities and their potential effects on operations and reputation.
Relying solely on annual attestations or audits for third parties often creates a "compliance illusion." Although PCI DSS requires yearly monitoring of service providers' compliance status, these assessments only capture a snapshot of the compliance status at a given point in time. Because cybersecurity threats are constantly evolving and cloud environments and data sharing protocols are continually changing, a vendor considered compliant today might introduce a new vulnerability or misconfiguration tomorrow. This dependence on periodic checks can lead organizations to believe they are compliant based on documentation. At the same time, the actual security of their supply chain could have significantly deteriorated since the last assessment.
This issue becomes even more significant when considering the cascading effect of Nth-party vulnerabilities on the PCI DSS scope. If a fourth-party cloud provider, used by a direct third-party payment processor, has a misconfigured storage bucket containing an organization's cardholder data (even temporarily), that Third-Party vulnerability directly affects the primary organization's PCI DSS compliance. That's because PCI DSS applies to anything that "may have an impact on the security of the cardholder data environment." The broad scope of the "impact" clause in PCI DSS encompasses these indirect relationships, meaning an organization's PCI DSS scope naturally extends to its critical sub-vendors, even without a direct contractual relationship. This dramatically increases the complexity of managing PCI DSS compliance and emphasizes the need for comprehensive visibility into the entire digital ecosystem, not just the first or second tier. The challenge is no longer just asking "who handles my data?" but instead, "who handles the data of those who handle my data, and what are their security practices?"
The Attacker's Advantage, Your Defense: Leveraging ThreatNG for Proactive PCI DSS Security
In response to the complex and changing challenges of securing the digital supply chain for PCI DSS compliance, ThreatNG provides a comprehensive and proactive solution. Its integrated features deliver unmatched visibility and continuous monitoring across an organization's entire digital ecosystem, including its direct third parties and the often-hidden Nth parties.
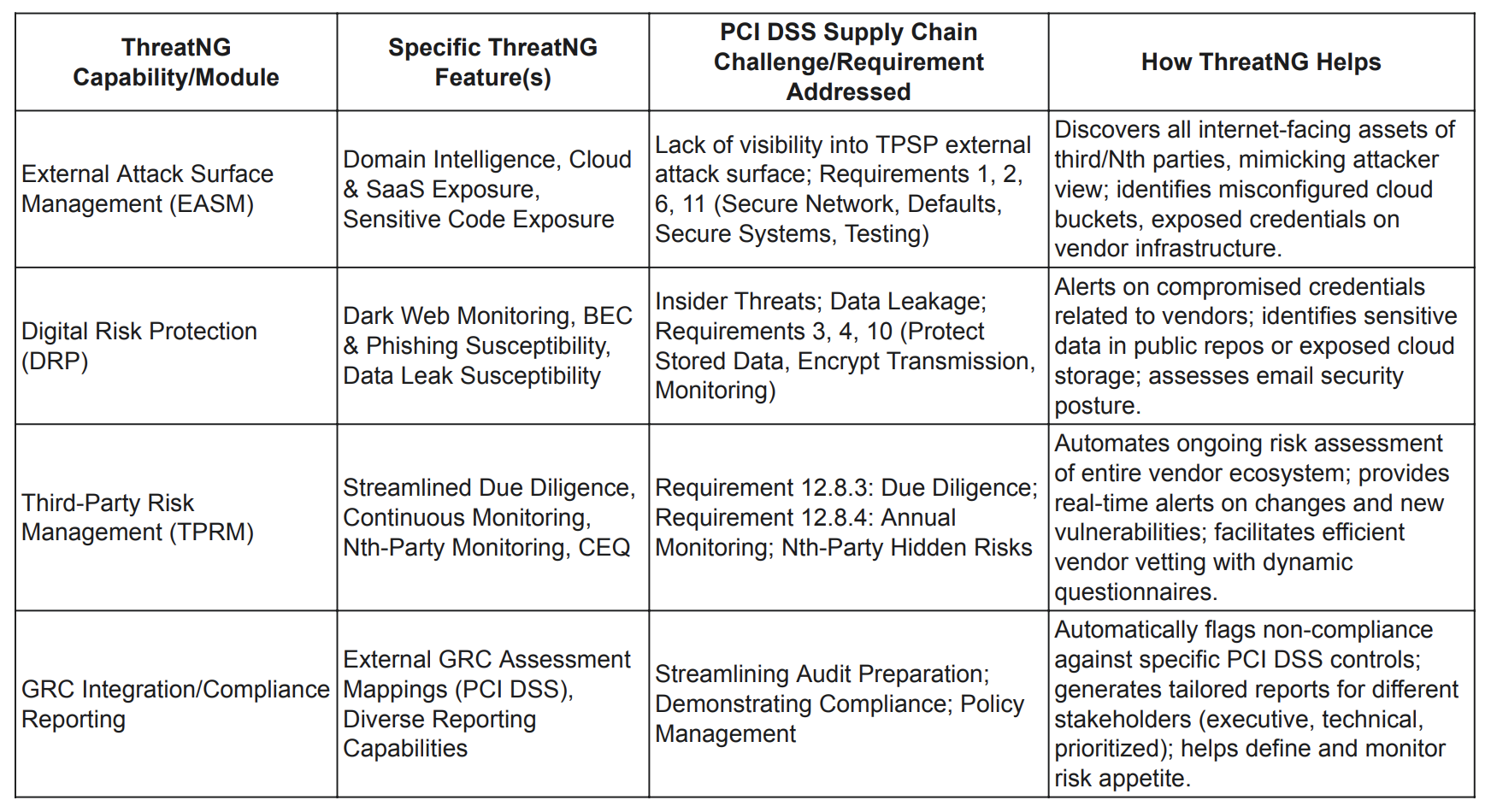
External Attack Surface Management (EASM)
ThreatNG redefines External Attack Surface Management by offering a comprehensive, "outside-in" approach to investigate and analyze an organization's entire digital exposure. It continuously detects and evaluates all potential entry points for external threats, including vulnerable systems, open ports, exposed services, and even accidentally accessible development environments. This "attacker's perspective" is crucial for PCI DSS compliance because it goes beyond the limitations of traditional vendor assessments, providing objective, verifiable evidence of external vulnerabilities within the supply chain that could result in a cardholder data breach. This approach enables proactive remediation and enhances compliance efforts, shifting the focus from merely trusting vendors to verifying their external security measures.
Key EASM capabilities include:
Domain Intelligence: This module identifies all assets associated with an organization and its third-party or Nth parties, revealing critical vulnerabilities such as misconfigured DNS records, weak certificates, and outdated software.
Cloud & SaaS Exposure: ThreatNG discovers and assesses cloud resources and SaaS applications, including protected, open, sanctioned, unsanctioned, and look-alike instances, without requiring agents, credentials, or API connections. This capability is crucial for identifying exposed open buckets, misconfigurations, and brand impersonations (cybersquats) that could compromise cardholder data.
Sensitive Code Exposure: The platform scans publicly available code repositories, mobile apps, and online sharing platforms for exposed credentials, passwords, configuration files, and API keys, which are common vectors for data breaches.
Archived Web Pages: ThreatNG analyzes archived versions of websites to identify old login pages or test environments that may still be accessible and contain exploitable vulnerabilities.
Technology Stack: By identifying the technologies in use by an organization and its partners, ThreatNG can assess whether they have known vulnerabilities or are end-of-life, requiring updates or replacements, which directly impacts Requirement 6 of the PCI DSS.
Digital Risk Protection (DRP)
ThreatNG's Digital Risk Protection (DRP) features provide a comprehensive approach to safeguarding an organization's digital assets against various risks by continually monitoring its online presence.
Early Warning of Threats: The platform monitors a vast amount of data, including leaked data and the dark web, to identify threats like data breaches, brand impersonation, and ransomware attacks before they can cause significant damage.
Dark Web Monitoring: ThreatNG discovers and inventories compromised credentials and ransomware events associated with an organization and its Nth parties on the dark web, providing critical intelligence for proactive defense.
BEC & Phishing Susceptibility: This assessment evaluates susceptibility to Business Email Compromise (BEC) and phishing attacks, utilizing sentiment analysis, financial data, dark web presence (for compromised credentials), and comprehensive email intelligence (including DMARC, SPF, DKIM, and harvested emails).
Data Leak Susceptibility: ThreatNG identifies exposed cloud storage buckets, compromised credentials on the dark web, and sensitive data in public code repositories, all of which are strong indicators of potential data leaks that could violate PCI DSS Requirement 3.
Comprehensive Third-Party and Nth-Party Risk Management (TPRM)
ThreatNG empowers organizations to proactively identify, assess, and mitigate risks across their entire vendor ecosystem, extending deep into Nth-party relationships.
Streamlined Due Diligence and Onboarding: ThreatNG allows organizations to quickly identify, manage, and monitor third-party risks, fulfilling essential due diligence requirements. By simply entering a third party's domain name, organizations can discover, evaluate, report on, and monitor their ethical, reputational, and cybersecurity risks. The Correlation Evidence Questionnaire (CEQ) dynamically creates customized questionnaires, greatly simplifying the assessment process.
Continuous Monitoring: A significant advantage over point-in-time annual assessments, ThreatNG offers ongoing, comprehensive oversight of an organization's third-party and Nth-party landscape. It tracks all identified assets and related risks, providing real-time alerts on changes, new vulnerabilities, or emerging threats. This shifts PCI DSS compliance from a periodic, burdensome task to a continuous, proactive security practice, enabling organizations to detect and address emerging risks in their supply chain before they turn into breaches or audit issues, delivering genuine assurance rather than just attestation.
Risk Assessment and Prioritization: ThreatNG evaluates and ranks external attack surface and digital risk findings using its "eXposure Priority" method. It carefully assesses the severity of each finding based on its potential impact, exploitability, and relevance, highlighting critical vulnerabilities such as subdomain takeover risk and web application hijack threats. Additionally, it offers detailed security ratings for each third-party and Nth-party.
Fourth-Party Supply Chain Monitoring: Crucially, ThreatNG explicitly supports the identification and monitoring of fourth-party vendors and beyond, which is essential for addressing the hidden risks posed by Nth parties that can cascade through the supply chain.
Simplified Compliance Reporting and GRC Integration
ThreatNG's detailed external assessments directly inform Governance, Risk, and Compliance (GRC) management by pinpointing specific vulnerabilities and digital risks across the extended enterprise.
External GRC Assessment Mappings: A key feature, ThreatNG automatically links its findings to specific controls within frameworks, such as PCI DSS. For example, if an exposed administrative interface or an unpatched vulnerability on a cardholder data environment is identified, the report instantly marks these as PCI DSS non-compliance issues. This capability significantly reduces the manual effort required to connect risks to compliance requirements, thereby accelerating GRC assessment and audit preparation.
Diverse Reporting Capabilities: ThreatNG offers a range of reporting options, including Executive, Technical, and Prioritized (High, Medium, Low, and Informational) reports, as well as Security Ratings, Inventory, and Ransomware Susceptibility reports, catering to the specific needs of various GRC stakeholders.
Policy Management: ThreatNG's customizable risk configuration enables tailoring risk scoring to an organization's specific needs, while dynamic entity definition provides a focused approach to critical assets, ensuring compliance with relevant policies.
The powerful synergy of ThreatNG's integrated modules, which enable complete PCI DSS compliance, is significant. While each module is practical on its own, together they form a comprehensive solution for PCI DSS supply chain security. For instance, External Attack Surface Management detects vulnerabilities on a third party's external attack surface. Digital Risk Protection then tracks leaked credentials or brand impersonations related to that third party on the dark web. Third-party risk management uses these insights for ongoing monitoring and due diligence. Finally, GRC integration automatically links these risks directly to PCI DSS requirements. This creates a continuous feedback loop that extends beyond isolated security functions, providing a unified view of risk and enabling more effective resource allocation, faster incident response, and a stronger overall compliance posture.
Table: ThreatNG Capabilities Mapping to PCI DSS Supply Chain Compliance
Implementing ThreatNG for Proactive PCI DSS Supply Chain Compliance
Implementing ThreatNG is more than just a technical deployment; it signifies a strategic shift toward ongoing security and compliance across an organization's extended enterprise. A phased approach can maximize its benefits for PCI DSS. This method encourages a fundamental change from a reactive "check-the-box" mentality to a proactive "secure-the-ecosystem" approach, fostering a strong security culture throughout the supply chain.
A Strategic Approach to Integrating ThreatNG
Phase 1: Discovery and Baseline: Start by using ThreatNG's advanced discovery features to map out the entire digital ecosystem. This includes identifying all known and previously unknown third parties. The goal is to establish a baseline for the initial security posture of all assets within this expanded scope.
Phase 2: Risk Assessment and Prioritization: Use ThreatNG's precise evaluation features to identify and rank vulnerabilities and digital risks throughout the supply chain. Remediation efforts should target findings with the most significant potential impact on cardholder data, guided by ThreatNG's "eXposure Priority" scoring.
Phase 3: Continuous Monitoring and Remediation: Conduct ongoing monitoring of the entire supply chain, utilizing ThreatNG's real-time alerts to manage changes, new threats, and compliance issues proactively. Developing transparent and collaborative remediation processes with vendors is key to effective risk mitigation.
Phase 4: Compliance Reporting and GRC Integration: Fully use ThreatNG's GRC mapping features to streamline PCI DSS audit preparation and demonstrate ongoing compliance. Create customized reports for various stakeholders, including technical teams and executive leadership, to ensure clear communication of the security posture.
Key Benefits
The strategic integration of ThreatNG offers several key benefits for organizations seeking to achieve PCI DSS compliance, extending beyond their immediate perimeter.
Enhanced Security Posture: ThreatNG enables proactive threat detection and prioritization, provides comprehensive attack surface mapping, and dramatically reduces the overall risk of cyberattacks across the digital ecosystem.
Reduced Risk of Breaches: By providing early identification of vulnerabilities and potential data leaks within the supply chain, ThreatNG helps minimize the impact on an organization's reputation and operations, safeguarding against costly data breaches.
Streamlined Compliance Efforts: Automated mapping of findings to PCI DSS requirements, simplified audit preparation, and continuous compliance assurance significantly reduce the manual burden and complexity of maintaining compliance.
Increased Customer Trust: Demonstrating a serious, proactive commitment to protecting cardholder data through robust supply chain security builds and maintains customer trust and confidence in an organization's ability to handle their financial transactions securely.
Improved Business Resilience: By implementing robust security controls and processes across the extended supply chain, ThreatNG contributes directly to the overall resilience and continuity of business operations, ensuring that payment processing remains uninterrupted even in the face of evolving threats.
Investing in a solution like ThreatNG for PCI DSS supply chain security is not just an expense; it's a strategic investment with a clear return on investment. The potential costs of a data breach, including reputational damage, legal liabilities, financial losses, and even the loss of the ability to process credit card transactions, greatly outweigh the investment in proactive security. By proactively identifying and reducing risks across the supply chain, ThreatNG helps prevent these disastrous outcomes. Additionally, the substantial decrease in manual effort needed to match risks to compliance requirements directly improves operational efficiency and saves costs during audit preparation. This makes the investment one that protects revenue, maintains brand reputation, minimizes legal and financial risks, and enhances compliance efforts, ultimately supporting the organization's long-term economic health and market position.
Secure Your Future: Embracing Continuous Supply Chain Security for PCI DSS Compliance
In today's interconnected digital world, securing cardholder data for PCI DSS compliance requires looking "Beyond the Perimeter" and adopting comprehensive supply chain security. The traditional focus on internal controls is inadequate considering the widespread nature of third-party and Nth-party risks. The primary entity ultimately bears responsibility for cardholder data security, making strong vendor oversight essential.
ThreatNG provides unparalleled visibility, continuous monitoring, and actionable intelligence across the entire digital ecosystem—an organization, its direct third parties, and even the hidden Nth parties in its supply chain. By seamlessly integrating External Attack Surface Management (EASM), Digital Risk Protection (DRP), and comprehensive Third-Party Risk Management (TPRM) with direct PCI DSS compliance mapping, ThreatNG transforms a complex, often reactive, challenge into a manageable, proactive security discipline. It effectively unmasks the risks lurking in your extended digital footprint.
By addressing PCI DSS compliance through a comprehensive, supply-chain-focused platform like ThreatNG, organizations not only solve a specific compliance issue but also tackle the larger challenge of supply-chain security. They are naturally building a stronger, more flexible, and complete cybersecurity program that benefits all parts of their digital operations and other compliance requirements. The platform’s ability to manage technical and business threats across the dark, deep, and open web, as highlighted by its "Security Centric; Not Exclusive" mantra, shows a wide range of its capabilities beyond just payment card data. This makes PCI DSS compliance not just a burden, but a strategic advantage that enhances overall security maturity.
ThreatNG enables organizations not only to meet explicit PCI DSS requirements but also to create a truly resilient and trustworthy environment for managing sensitive payment data. This proactive strategy protects reputation, maintains business continuity, and safeguards financial stability in an ever-changing threat landscape. To learn how ThreatNG can specifically address your PCI DSS supply chain security needs and reveal hidden risks within your digital ecosystem, it is highly recommended that you explore ThreatNG's capabilities further. Request a personalized demo today and take the definitive step "Beyond the Perimeter" toward ongoing, strong PCI DSS compliance.