June 23, 2025
ThreatNG Unleashes Major Updates: Elevating External Risk Management and Intelligence
ThreatNG is excited to announce a series of significant platform enhancements designed to provide unparalleled control, precision, and depth in understanding your external cyber risks. From customizable security ratings that align with your unique risk tolerance to granular control over code repository monitoring and a powerful new API for direct access to our vulnerability intelligence, these updates reinforce our commitment to proactive defense and actionable insights across your entire digital ecosystem.
Enhanced Security Ratings: ThreatNG Elevates External Risk Management with Customizable Scoring
Refining how you master digital risk, our enhanced Customizable Risk Scoring and Configuration at ThreatNG empowers you to align your Security Ratings precisely with your organization's unique risk tolerance—whether Averse, Minimalist, Cautious, Flexible, or Open. This critical capability moves beyond generic scores, allowing you to define and measure your external digital risk to the granular level across your entire digital environment, third parties, and supply chain.
With our refined contextual risk scoring, your Security Ratings aren't just numbers; they're actionable insights reflecting your specific priorities, business impact, and regulatory obligations. This enables external threat alignment and risk appetite orchestration, ensuring proactive defense for Brand Protection, Cloud & SaaS Exposure, Due Diligence, and Third-Party Risk Management.
Enhanced Code Repository Monitoring with Precise Control
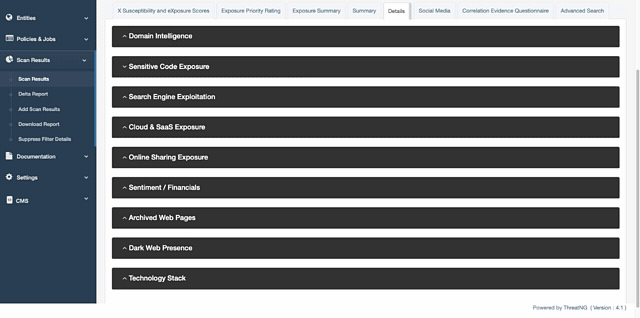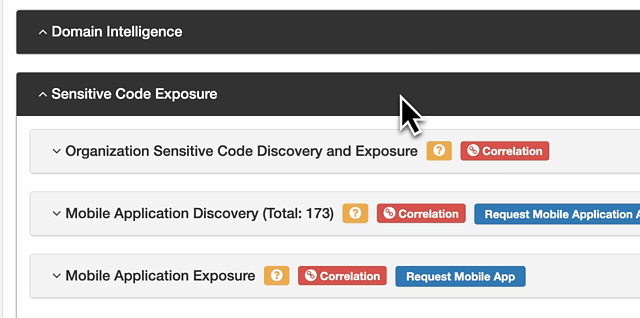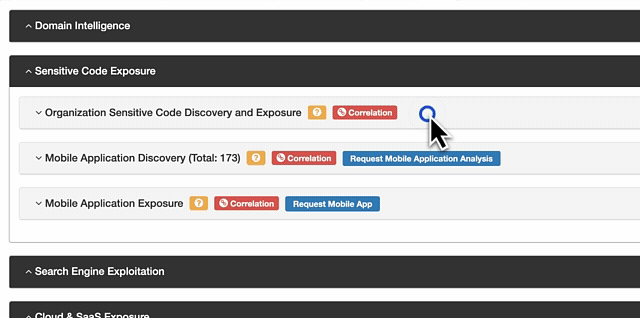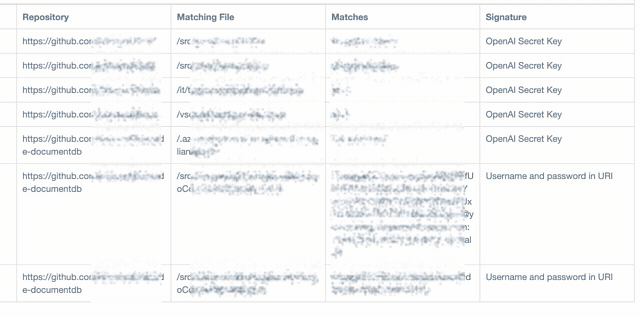
At ThreatNG, we're thrilled to announce a significant enhancement to our Code Repository Exposure module! You can now specify the public code repositories you want ThreatNG to discover, evaluate, and continuously monitor. This provides unparalleled control and accuracy over your code security posture, ensuring that these designated repositories do not unintentionally expose sensitive information.
This update means:
Targeted Oversight: Align monitoring precisely with your critical projects and vendor codebases.
Proactive Risk Mitigation: ThreatNG's External Discovery and External Assessment capabilities uncover and evaluate exposure. The Sensitive Code Exposure Investigation Module then thoroughly inspects the contents.
Continuous Vigilance: Our Continuous Monitoring ensures that new exposures are detected quickly.
Be proactive in protecting your software supply chain.
New API Endpoint: Unlocking Vulnerability Intelligence for Seamless Integration
ThreatNG is excited to launch a new API endpoint providing direct access to our DarCache Vulnerability intelligence repository. This powerful API integrates critical vulnerability data into your security workflows and platforms, including NVD, EPSS, KEV, and verified Proof-of-Concept (PoC) exploits.
Why it's Important: This API transforms DarCache Vulnerability into an adaptable intelligence feed, ensuring your prioritization and remediation are always backed by the latest, most contextualized real-world exploitability data.
Who Benefits:
SOC & IR Teams: Automate alert enrichment for faster triage and response.
Vulnerability Management Teams: Dynamically reprioritize findings based on external exploitability, focusing resources on critical threats.
MSSPs & Security Consultants: Enhance service offerings with proactive, contextualized vulnerability intelligence.
AppSec Teams: Integrate real-world exploitability into CI/CD pipelines to prioritize critical code flaws.
Organizations with Complex Supply Chains: Feed DarCache Vulnerability data into GRC/TPRM solutions to validate vendor security postures objectively.
This API empowers "Strategic Prioritization, Proactive Defense, and Informed Decision-Making" by bringing unparalleled exploit intelligence directly where it's needed most.
Continuous Evolution: Latest Platform Enhancements Revealed
Our commitment to providing unparalleled external security visibility at ThreatNG means constantly refining and expanding our capabilities. We're excited to announce the latest enhancements across our platform, designed to empower you with even greater clarity, deeper insights, and more actionable intelligence to protect your digital ecosystem.
These updates represent our dedication to staying ahead of evolving threats, ensuring ThreatNG remains your definitive source for external attack surface management, digital risk protection, and security ratings.
Security Ratings: Enhanced Presentation
Understanding your cyber risk posture is paramount, and communicating it effectively is just as crucial. We've refined the presentation of our Security Ratings to offer improved clarity and more intuitive visualizations. This enhancement ensures that whether you're a security analyst or an executive, you can quickly grasp your organization's risk profile, identify key areas of concern, and communicate progress with greater impact.
Reporting: Complete Brand Alignment with Enhanced White Label Customization
ThreatNG is excited to announce significant enhancements to our White Label Reporting feature. Now, you can seamlessly present our comprehensive security intelligence as a natural extension of your brand. Whether you're an internal team, a consultant, or a service provider, effortlessly present ThreatNG's powerful reports with your brand taking center stage. Leverage our industry-leading analysis and actionable insights, all while reinforcing your unique brand identity.
Intelligence Repositories (DarCache): Enhanced Financial Context with DarCache 8-K
Financial context often reveals underlying risks. Our DarCache Intelligence Repositories continue to provide critical insights, and we've refined our DarCache 8-K capabilities to deliver even richer financial context. This powerful repository consistently integrates U.S. SEC Form 8-Ks data directly into your risk assessments. By continuously analyzing these critical financial filings, ThreatNG provides proactive insights into an organization's declared material events, including cybersecurity incidents or financial strains that could impact their external risk profile.
Assessment: Validating Strengths with Positive Security Indicators
Security isn't just about finding weaknesses; it's also about recognizing and validating strengths. Our Positive Security Indicators assessment capability has been enhanced to provide a more balanced view of your security posture. This feature detects and highlights the presence of beneficial security controls and configurations, such as Web Application Firewalls or multi-factor authentication, validating their effectiveness from an external attacker's perspective. It helps you confidently showcase your resilient defenses.
Investigation Modules: Deeper Insights & Integrated Analysis
Our investigation capabilities have been further refined to offer more granular and interconnected analysis:
Subdomain Infrastructure Exposure: Our Subdomain Intelligence within the Domain Intelligence module now offers even deeper insights into Subdomain Infrastructure Exposure. This allows for a more granular understanding of technologies, services, and open ports residing on your subdomains, helping you uncover hidden risks and potential attack vectors often overlooked.
Mobile Application Discovery & Sensitive Code Exposure: These modules work in closer synergy. Beyond discovering mobile apps in marketplaces, ThreatNG delves deeper into analyzing their contents. Connecting to exposed code repositories uncovers sensitive data like hardcoded API keys, private keys, and other secrets within those mobile application contexts or linked code. This provides a comprehensive mobile app security assessment from an attacker's view.