September 10, 2025
Unmask Your Blind Spots: Secure Non-Human Identities & Streamline GRC Compliance
ThreatNG introduces two powerful new capabilities to help you gain control over your organization's security and compliance. The NHI Email Exposure feature addresses a silent yet critical vulnerability by highlighting non-human identities, such as service accounts and API keys, that traditional security tools often overlook. By continuously monitoring the web for exposed credentials, this feature helps you proactively discover and neutralize threats before they can be exploited. Simultaneously, our new GRC Mappings capability bridges the gap between security risks and compliance requirements by directly aligning external security findings with key regulatory standards, such as PCI DSS, making it easier for your teams to prioritize efforts and ensure compliance with confidence.
Eliminate Your #1 Security Blind Spot: Exposed Non-Human Identities
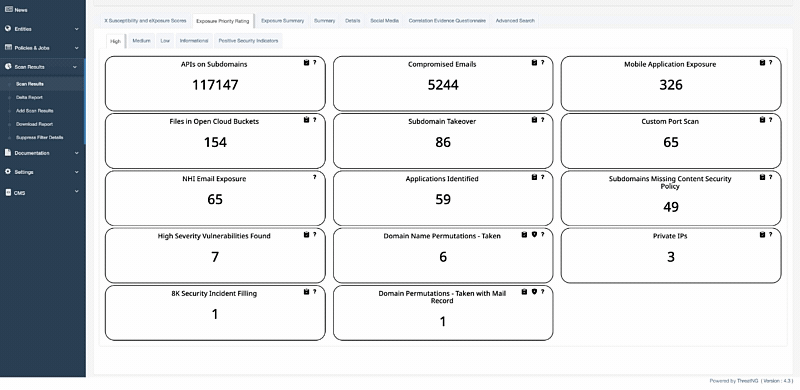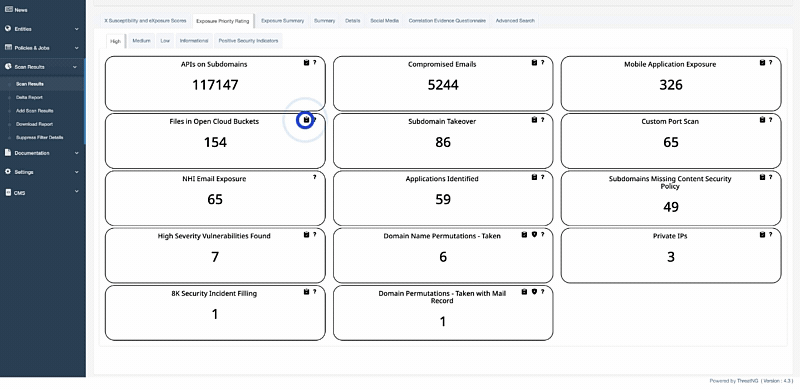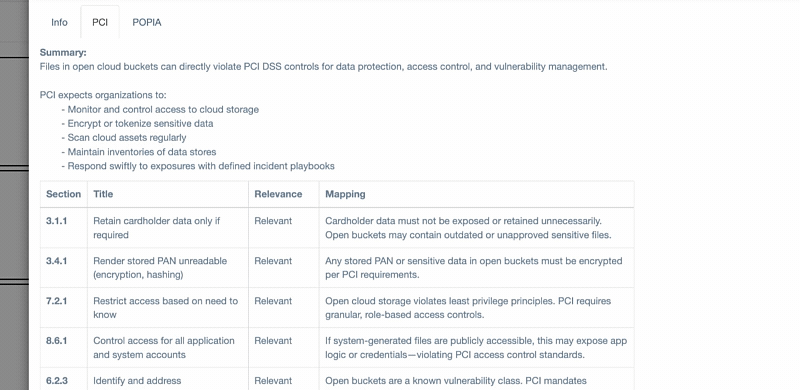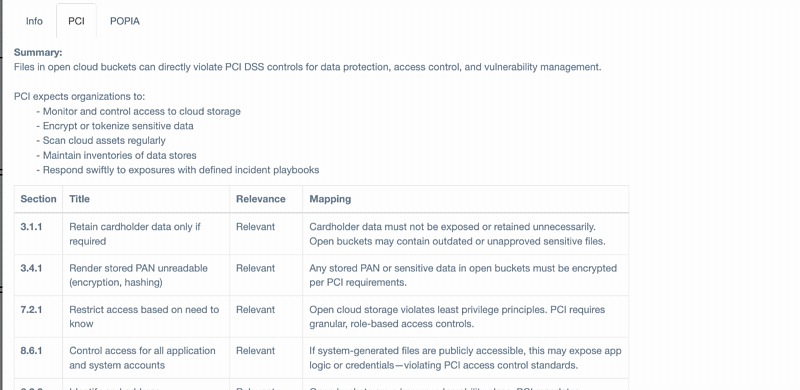
In the complex world of cybersecurity, a silent, critical vulnerability is often overlooked: the non-human identities (NHIs) that power your infrastructure. These service accounts, API keys, and machine identities are a primary entry point for sophisticated attacks, yet they remain a significant blind spot for traditional security tools. ThreatNG's new NHI Email Exposure capability is designed to transform your security posture from reactive to proactive, providing unparalleled visibility into these hidden risks. By continuously monitoring the surface, deep, and dark web, the platform discovers, prioritizes, and helps you mitigate high-value identity exposures before they can be exploited.
This capability is a game-changer for securing your business. It identifies and groups all exposed emails associated with key operational roles, such as admin@, devops@, and svc@, enabling security teams to focus on the threats that matter most. Instead of being overwhelmed by a flood of alerts, you get a single, prioritized list of critical risks, allowing you to shut down a key attack vector preemptively. With ThreatNG, you can take control of the Identity Exposure Gap, ensuring business continuity and reinforcing your team's vital role in protecting your organization.
ThreatNG's New GRC Mappings Bridge the Gap Between Security Risks and Compliance Requirements
ThreatNG is proud to announce the latest enhancement to its External GRC Assessment capability, which now provides direct mappings of external security findings to regulatory and industry standards such as PCI DSS within the "eXposure Priority Rating" view. This new feature offers a clear, actionable summary of your organization's security posture by identifying exposed assets, critical vulnerabilities, and digital risks from an attacker's perspective and then aligning these findings with specific GRC framework requirements. Each finding is presented with its level of relevance—Relevant, Indirectly Relevant, Partially Relevant, or Tangential—and an explanation of the mapping, enabling GRC and security teams to prioritize efforts and ensure efficient proactive compliance with key standards. This new capability enables organizations to uncover and address external security and compliance gaps, thereby strengthening their overall GRC posture.