September 26, 2025
Your Peace of Mind, Secured: ThreatNG Unifies Risk, Compliance, and Cloud Visibility
In today's intricate digital world, security professionals face ongoing challenges against uncertainty. The fear of expensive breaches, concerns about compliance failures, and anxiety over unknown vulnerabilities can be overwhelming. ThreatNG aims to change that. We are excited to introduce major improvements to our platform that will revolutionize your security approach, shifting you from reactive worry to proactive confidence. Our newest updates to External GRC Assessment, SaaS Discovery, and Advanced Search are created to provide you with complete visibility and precise control to safeguard your organization and achieve true peace of mind.
From Unknown Threats to Confident Compliance: ThreatNG Expands GRC Assessment with HIPAA & GDPR
ThreatNG's External GRC Assessment has been expanded to include mappings for HIPAA and GDPR. This enhancement provides a continuous, outside-in evaluation of an organization's Governance, Risk, and Compliance posture from the perspective of an unauthenticated attacker.
Why This Matters
This new capability is a powerful tool for organizations that handle sensitive data, as it allows them to proactively identify and address security and compliance gaps before they become costly breaches.
For Healthcare Organizations: The addition of HIPAA mapping is critical for any entity that creates, maintains, or transmits Protected Health Information (PHI). This includes hospitals, clinics, and business associates (such as vendors and IT providers) who must comply with stringent security rules. This feature helps these organizations demonstrate due diligence and protect patient trust, which is invaluable.
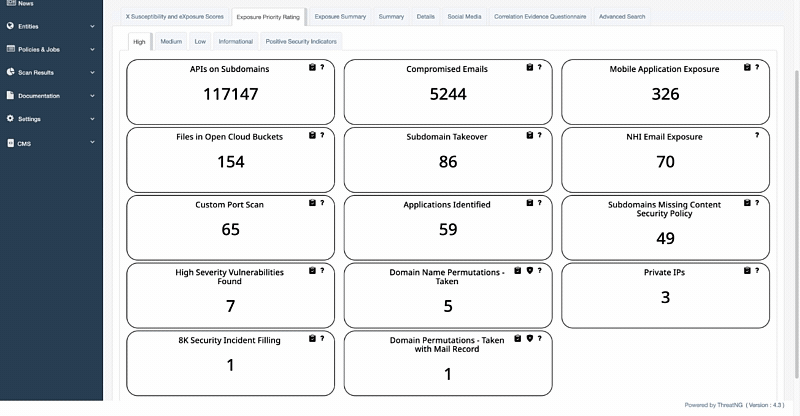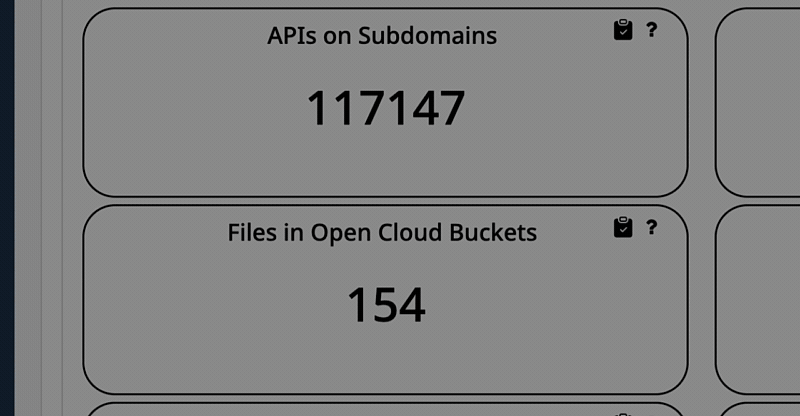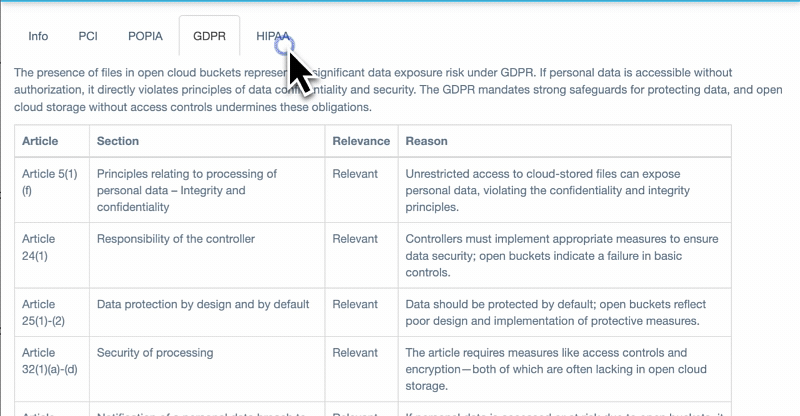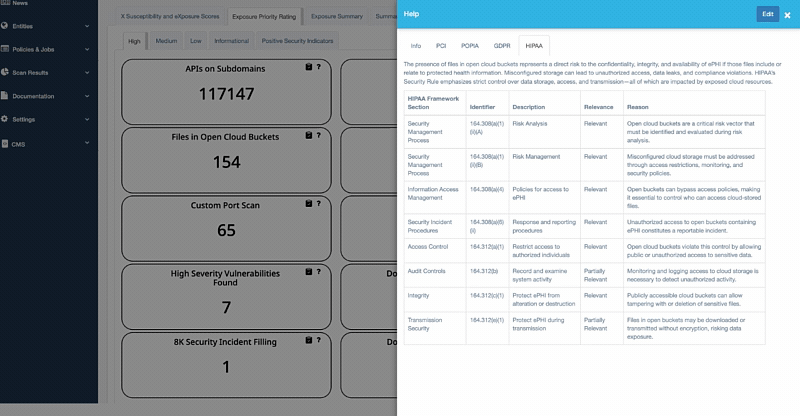
For Organizations Handling EU Data: The GDPR mapping is essential for any company that processes the personal data of EU residents, regardless of the company's location within the EU. This capability enables organizations to comply with GDPR requirements, which include implementing data protection measures proportionate to the risk and conducting assessments for high-risk data processing activities. This helps prevent severe penalties of up to €20 million or 4% of global annual revenue.
ThreatNG's External GRC Assessment aligns your security posture with external threats by identifying vulnerabilities and exposures in the same way a malicious actor would, directly mapping these findings to the relevant GRC frameworks. This approach empowers security, compliance, and risk management teams to identify and resolve issues that others may overlook, providing peace of mind and confidence in their security posture.
Goodbye, Shadow IT: ThreatNG Expands SaaS Discovery with Aha, Duo, Snowflake, and More
It is with immense excitement that ThreatNG announces the addition of Aha, Axonious, Brandfolder, Duo, Greenhouse, and Snowflake to its SaaS Discovery capabilities within the Cloud and SaaS Exposure Investigation Module. This is more than just a list of new names; it's a profound step forward in helping you regain control and have peace of mind over your organization's digital security.
The Fear of the Unknown
In today's fast-paced business environment, the fear of the unknown is a constant threat. Your organization's SaaS footprint is rapidly expanding, and with it, the risk of Shadow IT—unsanctioned or unmanaged applications that can create dangerous blind spots in your security posture. This can lead to a nagging worry: What are we missing? What are we unknowingly exposing to the world? This lack of visibility is a significant blind spot for security teams, allowing attackers to discover and exploit these exposures before they are even identified.
The Confidence of Complete Visibility
This is where the new additions to our SaaS discovery become so powerful. We're giving you the confidence that comes with a complete and accurate inventory of your sanctioned and unsanctioned SaaS services. We help you find and fix what others can't. By uncovering your full digital footprint from the perspective of an attacker, we help you identify potential risks and misconfigurations before they can be exploited. This is especially crucial for security, compliance, and risk management teams who need to demonstrate a comprehensive understanding of their organization's external attack surface. You can stop worrying about what's lurking in the shadows and instead feel empowered to manage your risk proactively.
This expanded capability is a game-changer for businesses that rely on these specific platforms for critical functions, such as human resources (Greenhouse), project management (Aha), and data analytics (Snowflake), as well as those managing identity and access (Duo). By providing a unified, outside-in view, ThreatNG enables you to protect sensitive data and maintain business continuity, giving you the peace of mind you deserve.
Precision in a Sea of Data: ThreatNG Advanced Search Now Features Wildcards & Version Pinpointing
We understand the frustration of sifting through endless data, searching for a single, crucial detail that could mean the difference between a secure environment and a costly breach. That's why we are thrilled to announce a powerful enhancement to ThreatNG's Advanced Search capability: the addition of wildcard searches and the ability to search for specific versions of technologies.
This isn't just a technical upgrade; it's about giving you the control and precision you've been craving. You can now leave behind the anxiety of incomplete searches and embrace the confidence of finding precisely what you need, exactly when you need it.
Why This Matters
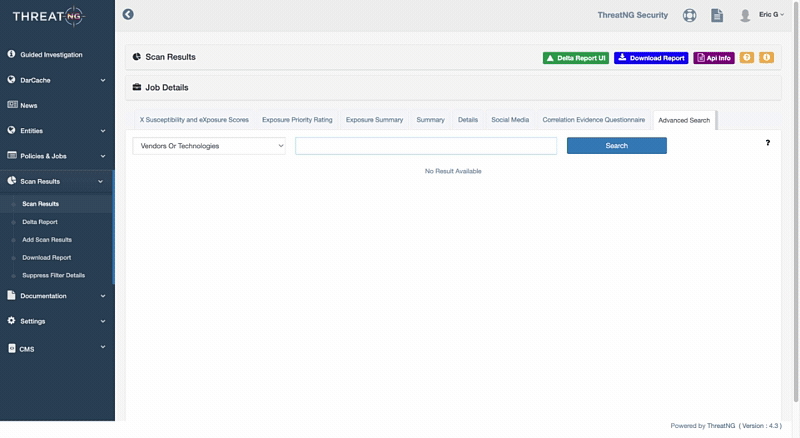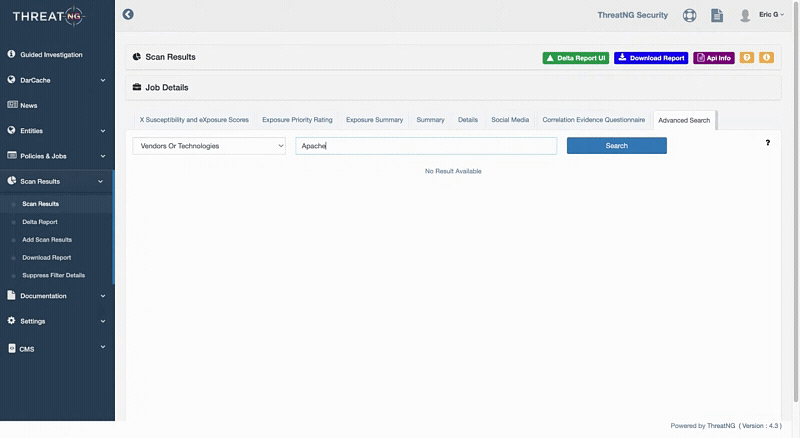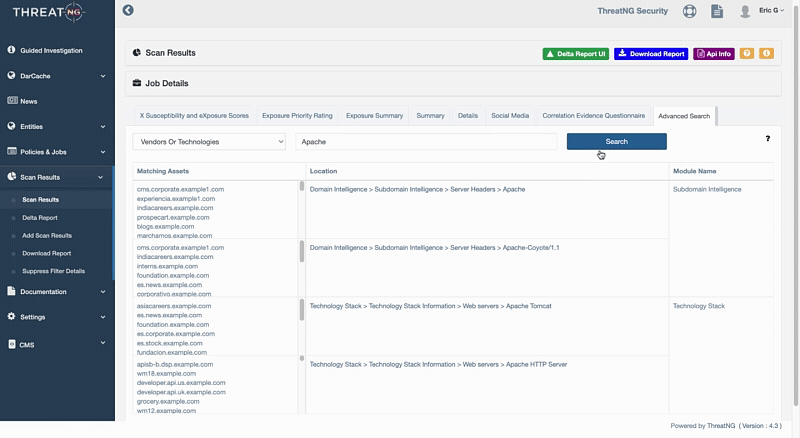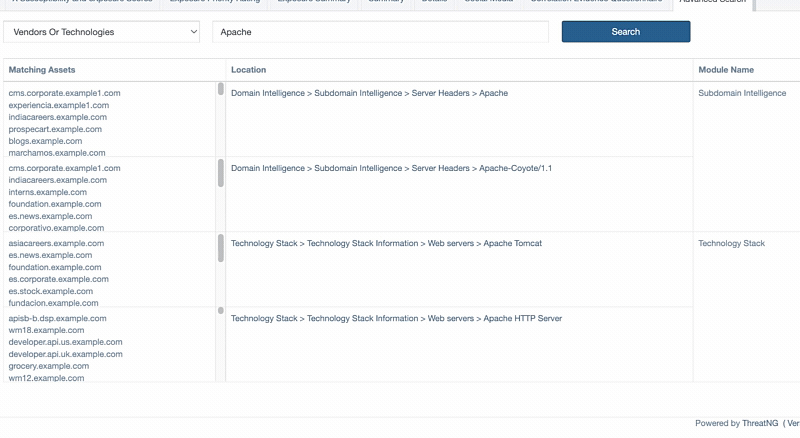
This new capability is a game-changer for security analysts, threat hunters, and risk management teams who need to conduct detailed investigations. The ability to use wildcard characters means you can quickly uncover a broader range of related findings on your external attack surface, even with partial information. For example, you can now search for Apache to find all versions of Apache web servers. This saves valuable time and ensures that nothing is missed.
Furthermore, being able to search for specific technology versions gives you the power to pinpoint critical vulnerabilities with unprecedented accuracy. Knowing that your organization uses a specific, outdated version of a software package like "Nginx" allows you to proactively address the exact risks associated with it, instead of wasting time on broad, unconfirmed threats. This level of precision is invaluable for prioritizing remediation efforts and making more intelligent, more effective security decisions.
ThreatNG's Advanced Search already helps you quickly find specific data, extract intelligence, and identify risks. These new features empower you to take your investigations to the next level, transforming uncertainty into actionable intelligence and giving you the peace of mind that comes with complete visibility.