Email Address Enumeration
In cybersecurity, email address enumeration is a technique where an attacker attempts to discover valid email addresses associated with a specific domain or organization. It's a form of reconnaissance that aims to gather detailed information about a target system before launching more advanced attacks.
How Email Address Enumeration Works
Attackers use various methods to perform email address enumeration, often exploiting subtle differences in system responses:
Login Form Responses: Many websites or applications provide error messages depending on whether the entered email address is valid or invalid. For example:
Entering an invalid email might return "Email not found."
Entering a valid email with an incorrect password might return "Incorrect password."
This distinction allows an attacker to deduce which email addresses exist.
Password Reset Features: Password reset functionalities can reveal valid email addresses, such as those found in login forms. If an attacker requests a password reset for an email that doesn't exist, the system might say "Email not found," whereas for a valid email, it might say "If this email exists, a reset link has been sent" (even if no link is sent for an invalid email).
Account Registration Feedback: Some systems will indicate if an email address is already registered when attempting to register a new account. This confirms the existence of that email.
SMTP Probing: Attackers can directly interact with the Simple Mail Transfer Protocol (SMTP) server. By sending commands like
VRFY(verify user),EXPN(expand mailing list), orRCPT TO(recipient to), they can check if a specific email address exists on the server. A "250 OK" response typically means the address exists, while a "550 No such user" indicates it doesn't.Timing Attacks: Even if error messages are generic, attackers might observe subtle differences in server response times. For example, a valid email address might take slightly longer to process than an invalid one, providing a clue about its existence.
Open-Source Intelligence (OSINT) and Public Data: Attackers can scour public sources like social media, LinkedIn, company websites, data breaches, and archived web pages (e.g., Wayback Machine) to collect potential email addresses. They then use enumeration techniques to verify which ones are active.
Common Email Formats: Many organizations use predictable email formats (e.g.,
firstname.lastname@company.com,firstinitiallastname@company.com). Attackers can guess these formats and then test them.
Risks and Consequences of Email Address Enumeration
While email enumeration itself doesn't directly compromise accounts, it's a crucial first step for more serious attacks:
Phishing and Social Engineering: Knowing valid email addresses allows attackers to craft highly targeted and convincing phishing emails. These emails can be designed to trick recipients into revealing sensitive information, clicking malicious links, or downloading malware.
Credential Stuffing and Brute-Force Attacks: With a list of valid email addresses, attackers can combine them with known passwords from data breaches (credential stuffing) or attempt to guess passwords (brute-force attacks) to gain unauthorized access to accounts.
Account Takeover (ATO): If an attacker confirms a valid email address and then successfully obtains the corresponding password, they can take over the user's account.
Increased Spam and Malware: Enumerated email addresses can be added to spam lists or used for distributing malware.
Business Email Compromise (BEC): Valid employee email addresses are valuable for BEC scams, where attackers impersonate executives or trusted individuals to defraud the company.
Prevention and Mitigation
Organizations can implement several measures to prevent or mitigate email address enumeration:
Generic Error Messages: Configure systems to return consistent, generic error messages for valid and invalid email addresses. For example, instead of "Email not found," use "If an account is associated with that email, a reset link has been sent."
Rate Limiting: Implement rate limiting on login forms, password reset pages, and other API endpoints to restrict the number of attempts from a single IP address or user within a given timeframe.
CAPTCHA: Use CAPTCHA or reCAPTCHA to prevent automated bots from performing enumeration attempts.
Obscure SMTP Responses: Configure email servers to provide generic error messages instead of revealing whether an email address exists when probed via SMTP commands.
Multi-Factor Authentication (MFA): Even if an attacker enumerates an email address and guesses a password, MFA adds an extra layer of security by requiring a second form of verification.
Monitor for Enumeration Attempts: Regularly monitor server logs for suspicious patterns of repeated email lookups or login attempts from unusual sources.
Conceal Personally Identifiable Information (PII): Avoid exposing unmasked PII in public-facing interfaces.
Randomize Server Response Times: To counter timing attacks, introduce artificial delays or randomize server response times for different outcomes (valid vs. invalid email).
Secure Identity Frameworks: Use modern identity frameworks with built-in features to mitigate enumeration risks.
ThreatNG, an all-in-one external attack surface management, digital risk protection, and security ratings solution, provides comprehensive capabilities that directly address and help mitigate the risks associated with email address enumeration.
ThreatNG's Role in Countering Email Address Enumeration:
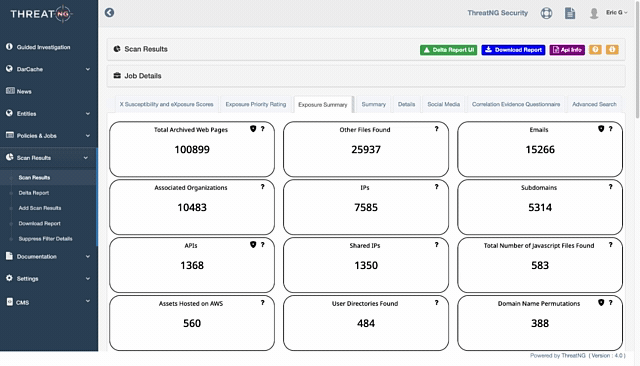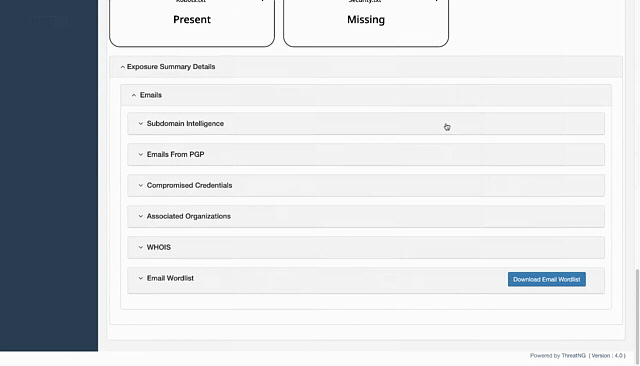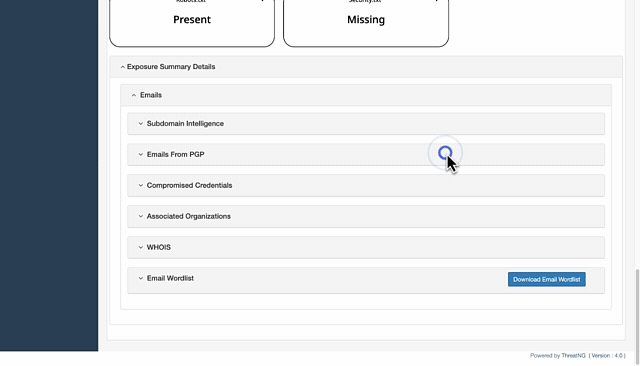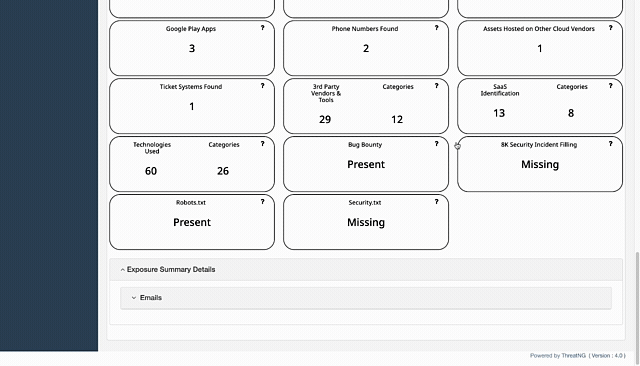
1. External Discovery: ThreatNG can perform purely external, unauthenticated discovery. This means it can identify email addresses and related information from an attacker's perspective without requiring any internal access or connectors. By discovering publicly exposed email addresses, ThreatNG helps organizations understand their attack surface and identify potential enumeration vectors.
2. External Assessment - BEC & Phishing Susceptibility: ThreatNG provides an "External Assessment" capability, specifically assessing "BEC & Phishing Susceptibility." This assessment directly addresses the primary risk of email enumeration. It is derived from:
Domain Intelligence (Email Intelligence): ThreatNG's Domain Intelligence includes "Email Intelligence," which provides "email security presence and format prediction". This capability can identify standard email address formats that an organization uses, which attackers often guess during enumeration. It also assesses the presence of email security measures like DMARC, SPF, and DKIM records. For example, if an organization has weak SPF records, it could be easier for an attacker to spoof emails and make enumeration attempts less noticeable. ThreatNG would highlight this vulnerability, allowing the organization to strengthen its email security.
Dark Web Presence (Compromised Credentials): Email enumeration often leads to credential stuffing. ThreatNG's assessment factors in "Compromised Credentials" found on the dark web. If an organization's email addresses are found in data breaches, ThreatNG can flag this, indicating that these enumerated addresses are at higher risk for credential stuffing attacks.
3. Reporting: ThreatNG offers various reporting capabilities, including "Ransomware Susceptibility" and "Security Ratings". These reports can highlight the impact of email address enumeration by showing how exposed email addresses contribute to an organization's overall risk posture. For instance, a report might show a high "BEC & Phishing Susceptibility" score directly linked to identified email address exposures and provide "Recommendations" on reducing this risk.
4. Continuous Monitoring: ThreatNG provides "Continuous Monitoring" of an organization's external attack surface and digital risk. This is crucial for detecting ongoing email enumeration attempts. If new email addresses or unexpected patterns of email-related exposures appear, ThreatNG can alert the organization, allowing for a rapid response. For example, if a new, previously unknown subdomain containing email addresses suddenly appears, ThreatNG's continuous monitoring would detect this and flag it as a potential risk.
5. Investigation Modules: ThreatNG's "Investigation Modules" offer deep insights that are invaluable for understanding and mitigating email address enumeration:
Domain Intelligence: This module is central to understanding email enumeration risks.
Email Intelligence: This specific capability within Domain Intelligence directly helps with email enumeration. It provides "Format Predictions" for email addresses, which can be cross-referenced with enumerated addresses to determine if they align with the organization's standard format. It also offers "Harvested Emails," which means ThreatNG actively identifies and collects publicly available email addresses associated with the target. For example, if ThreatNG harvests a large number of emails from an organization's public website that follow a predictable pattern (e.g.,
firstname.lastname@company.com), it provides concrete evidence of enumeration susceptibility.DNS Intelligence (Domain Name Permutations): ThreatNG identifies "Domain Name Permutations (Taken and Available)". Attackers often create similar-looking domain names for phishing attacks after enumerating legitimate email addresses. ThreatNG can identify these lookalike domains, helping to pre-emptively detect potential phishing campaigns that would use enumerated addresses.
Subdomain Intelligence: This module can identify Emails found within subdomains. If an attacker is enumerating email addresses by crawling an organization's subdomains, ThreatNG can proactively discover these exposed email addresses, helping the organization secure those subdomains.
Search Engine Exploitation (Robots.txt and Security.txt Analysis): ThreatNG discovers website control files like
robots.txtandsecurity.txt. These files can inadvertently expose "Email Directories," "Emails Found," or "Contact Information Found". ThreatNG's analysis of these files helps identify unintentional disclosures that facilitate enumeration. For instance, if arobots.txtfile is misconfigured and exposes a directory containing employee contact information, ThreatNG will highlight this.Archived Web Pages: ThreatNG can analyze "Archived Web Pages" for "Emails". This helps discover historical email exposures that might still be valid, providing attackers with a larger pool of targets.
Dark Web Presence (Compromised Credentials): As mentioned in the External Assessment, this module provides concrete evidence of "Compromised Credentials". If an attacker has enumerated email addresses and then uses them in credential stuffing attacks, and some of those credentials are found on the dark web, ThreatNG can correlate this information, confirming the enumeration's effectiveness.
6. Intelligence Repositories (DarCache): ThreatNG's "Intelligence Repositories," branded as DarCache, provide constantly updated data that enriches its ability to combat email enumeration:
Compromised Credentials (DarCache Rupture): This repository contains "Compromised Credentials". By cross-referencing enumerated email addresses with this repository, ThreatNG can identify which of an organization's email accounts have already been exposed in data breaches, allowing for proactive password resets or MFA enforcement.
Dark Web (DarCache Dark Web): This repository tracks "Organizational mentions of Related or Defined People, Places, or Things, Associated Ransomware Events, Associated Compromised Credentials". If email addresses are being discussed or traded on dark web forums due to enumeration, ThreatNG can detect these mentions, providing early warning of potential attacks.
Complementary Solutions and Synergies:
While ThreatNG provides robust capabilities for email enumeration detection and mitigation, it can work synergistically with other cybersecurity solutions:
Security Information and Event Management (SIEM) Systems: ThreatNG's comprehensive reporting and continuous monitoring capabilities can feed valuable intelligence into a SIEM system. For example, if ThreatNG identifies a surge in potential email enumeration attempts targeting an organization's login page, it could alert the SIEM. The SIEM could then correlate this with other logs, such as failed login attempts or unusual network traffic, to provide a more holistic view of the potential attack.
Security Orchestration, Automation, and Response (SOAR) Platforms: When ThreatNG detects a confirmed email enumeration event or a high susceptibility to phishing due to exposed emails, it can trigger automated playbooks in a SOAR platform. For instance, if ThreatNG identifies a significant number of harvested emails from a specific domain, the SOAR platform could automatically initiate steps like blocking IP addresses known for enumeration, forcing password resets for affected users, or triggering targeted user awareness training.
Threat Intelligence Platforms (TIPs): ThreatNG's DarCache intelligence repositories, especially "Compromised Credentials (DarCache Rupture)" and "Dark Web (DarCache Dark Web)", can enrich a central TIP. This allows the organization to consolidate threat intelligence from various sources, providing a more comprehensive understanding of the threats posed by enumerated email addresses and associated risks. For example, if ThreatNG identifies specific email formats or patterns being targeted, this information can be added to the TIP for broader organizational defense.
Identity and Access Management (IAM) Solutions: ThreatNG identifies harvested or compromised email addresses, which directly informs IAM strategies. If ThreatNG flags specific user emails as high-risk, the IAM solution can enforce stricter access controls for those accounts, such as mandatory MFA or adaptive authentication based on user behavior.
ThreatNG acts as a robust front-line defense against email address enumeration by actively discovering exposed email addresses, assessing the susceptibility to attacks that rely on them, continuously monitoring for new exposures, and providing detailed intelligence and reporting to enable proactive mitigation. Its synergies with complementary solutions strengthen an organization's overall cybersecurity posture against this fundamental reconnaissance technique.