Email Address Harvesting
In the context of cybersecurity, Email Address Harvesting (also known as email scraping) refers to the automated or manual process of collecting large lists of email addresses, often without the consent of the email address owners. These harvested lists are then typically used for malicious purposes, primarily spamming, phishing attacks, and other forms of cybercrime.
Here's a detailed breakdown:
How Email Address Harvesting Works
Attackers use various methods to obtain email addresses:
Web Scraping Bots/Harvesters: This is one of the most common methods. Automated programs (bots or spiders) crawl websites, forums, social media platforms, online directories, public databases (like WHOIS for domain registrations), and even Usenet archives. They scan HTML content, text, contact forms, and metadata to extract any string resembling an email address.
Directory Harvest Attacks (DHAs): Attackers try to guess valid email addresses at a specific domain by sending emails to common usernames (e.g.,
info@domain.com,admin@domain.com,john.doe@domain.com) and analyzing the server's responses. A "non-delivery report" (NDR) or a bounced email indicates an invalid address, allowing the harvesters to refine their list to include only valid ones.Purchasing/Trading Lists: Cybercriminals often buy or trade pre-compiled lists of email addresses on the dark web or from other spammers. These lists might be compiled through various illicit means, including data breaches.
Malware and Viruses: Some malware can scan a compromised computer's hard drives, email clients, or network traffic for email addresses stored locally or exchanged over the network. These harvested addresses are then sent back to the attacker.
Social Engineering: Attackers use deceptive tactics, such as fake online surveys, contests, or "free product/service" offers, to trick individuals into voluntarily providing their email addresses.
Compromised Websites/Databases: If a website or online service is breached, attackers can gain access to databases containing user email addresses.
Publicly Available Information: Individuals often post their email addresses on public platforms (e.g., resumes, academic papers, online profiles), making them easy targets for harvesters.
Impact of Email Address Harvesting
The consequences of email address harvesting can be significant for individuals and organizations:
Spamming: The most direct and typical result is an increase in unsolicited bulk emails (spam). This can overwhelm inboxes, waste time, and consume network resources.
Phishing Attacks: Harvested email addresses provide attackers with valid targets for phishing campaigns. These emails, often crafted to appear legitimate, aim to trick recipients into revealing sensitive information (passwords, financial details) or clicking on malicious links that install malware.
Social Engineering Attacks: Knowing a person's email address can be the first step in more sophisticated social engineering attempts. Attackers might use the address to research the individual or organization, impersonate trusted entities, and build credibility for targeted attacks.
Identity Theft and Fraud: Combined with other harvested data, email addresses can be used to facilitate identity theft, account takeovers, and various forms of financial fraud.
Data Privacy Violations: The collection of email addresses without consent can violate data protection laws and regulations (e.g., GDPR, CAN-SPAM Act). This can lead to legal penalties, fines, and reputational damage for organizations.
Reputational Damage: For businesses, if their employees' or customers' email addresses are harvested from publicly accessible sources, it can erode trust and damage the organization's reputation.
Increased Security Risks: An extensive list of valid email addresses makes it easier for attackers to launch broader attacks against an organization, testing vulnerabilities and improving the overall attack surface.
Prevention and Mitigation
While it's challenging to prevent email harvesting completely, several measures can help minimize the risk:
Avoid Publicly Displaying Email Addresses: Do not publish plain-text email addresses on websites, forums, or social media.
Use Contact Forms: Implement secure contact forms on websites instead of directly displaying email addresses.
Obfuscate Email Addresses: If an email address must be displayed, use techniques like:
Image-based addresses: Display the email address as an image.
JavaScript obfuscation: Use JavaScript to dynamically generate or display the email address, making it harder for bots to scrape.
HTML character entities: Encode characters (e.g.,
user@example.comforuser@example.com).Human-readable formats: Spell out parts of the address (e.g.,
user [at] example [dot] com).
Implement Spam Filters: Utilize robust email filtering systems at both the server and client levels to detect and block incoming spam and phishing attempts.
Educate Users: Train employees and users about the risks of email harvesting, how to identify suspicious emails, and best practices for online privacy.
Two-Factor Authentication (2FA): Enable 2FA on email accounts and other online services to add an extra layer of security against unauthorized access, even if credentials are compromised.
Monitor for Suspicious Activity: Organizations should regularly monitor their networks and email servers for unusual patterns that may indicate harvesting attempts, such as a high volume of requests for invalid email addresses.
Limit Information Exposure: Be mindful of the personal and professional information shared online, as harvesters can aggregate it.
Directory Harvest Attack Prevention: Configure mail servers not to reveal information about valid email addresses during SMTP conversations. For example, by providing a generic error message for invalid recipients instead of explicitly stating that the address doesn't exist.
By understanding the methods and implications of email address harvesting, individuals and organizations can take proactive steps to protect their email addresses and mitigate associated cybersecurity risks.
ThreatNG, as an all-in-one external attack surface management, digital risk protection, and security ratings solution, offers comprehensive capabilities to combat email address harvesting and its associated risks.
External Discovery
ThreatNG excels at purely external, unauthenticated discovery, meaning it can find and analyze an organization's digital footprint without needing any internal connectors. This is crucial for identifying publicly exposed email addresses. It would achieve this by:
Crawling and Scraping: ThreatNG's external discovery would behave much like an attacker's harvesting bot, albeit for defensive purposes. It would crawl websites, subdomains, and other online presences associated with the organization. In doing so, it would identify email addresses explicitly published on web pages, in documents, or within HTML code. For instance, if an "About Us" page lists
info@example.comin plain text, ThreatNG's discovery would flag it.Subdomain Enumeration: By identifying all associated subdomains, ThreatNG might uncover forgotten or misconfigured subdomains that contain publicly exposed email addresses.
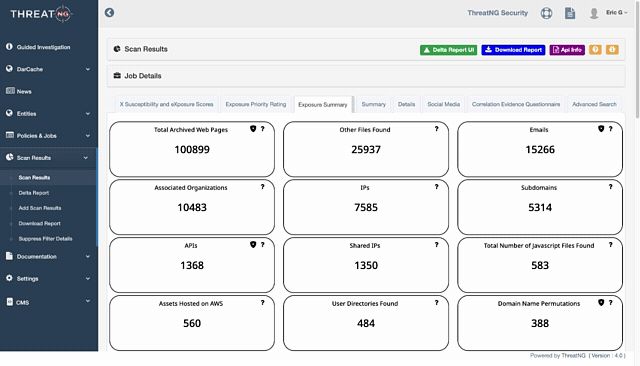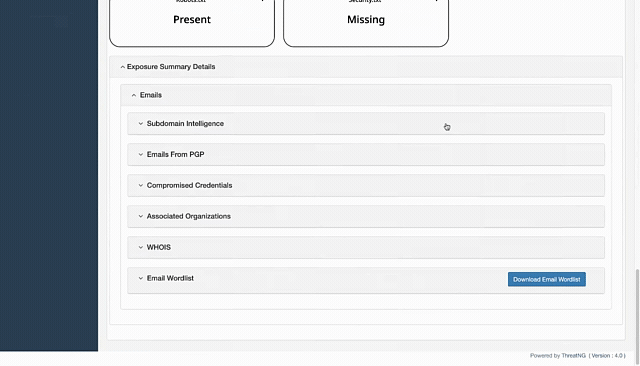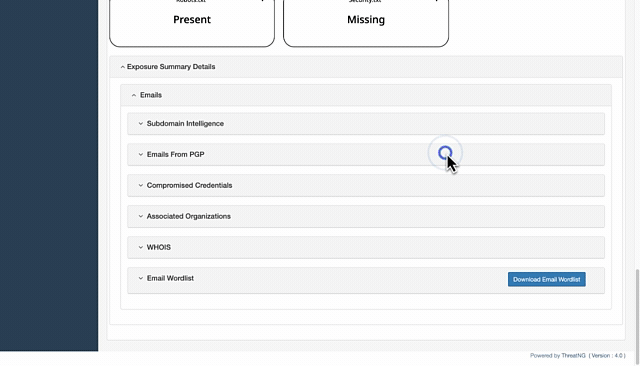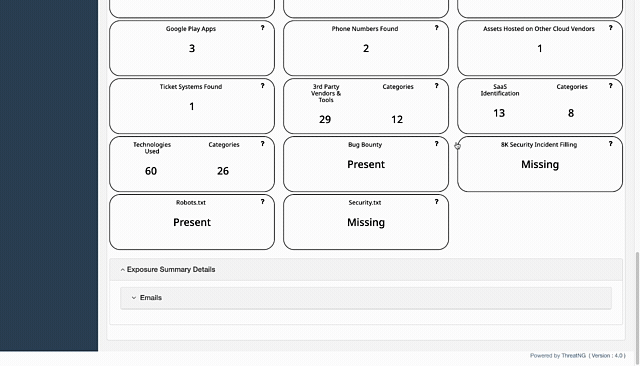
Archived Web Pages: ThreatNG can discover emails found within archived web pages related to the organization's online presence. This means if an email address was removed from a live site but remains in an archived version, ThreatNG could still find it.
Search Engine Exploitation: ThreatNG can assess an organization's vulnerability to exposing user data and emails through search engines. It can detect emails found within
robots.txtfiles andsecurity.txtfiles, which attackers often use to find exposed information.
External Assessment
ThreatNG performs various external assessments that indirectly and directly highlight susceptibility to risks stemming from email address harvesting:
BEC & Phishing Susceptibility: This assessment directly addresses a significant risk of email harvesting. ThreatNG derives this score from "Domain Intelligence" which includes "Email Intelligence" capabilities such as email security presence (DMARC, SPF, and DKIM records) and format prediction. It also uses "Dark Web Presence" (compromised credentials).
Example: If ThreatNG identifies that an organization's email domain lacks proper SPF, DKIM, or DMARC records, it would highlight a higher susceptibility to BEC (Business Email Compromise) and phishing attacks, as it's easier for attackers to spoof emails from that domain using harvested addresses. If ThreatNG identifies numerous compromised credentials associated with the organization's email addresses on the dark web, it significantly increases the BEC & Phishing Susceptibility score.
Data Leak Susceptibility: This assessment factors in "Dark Web Presence" (compromised credentials) and "Email Intelligence" that provides email security presence and format prediction.
Example: If ThreatNG discovers a large number of organizational email addresses alongside passwords on dark web forums, it indicates a high susceptibility to data leaks, making those harvested emails more valuable to attackers.
Brand Damage Susceptibility: Harvested email addresses can be used in campaigns that tarnish a brand's reputation, potentially leading to significant damage. ThreatNG considers "Sentiment and Financials" (including negative news) and "Domain Intelligence" (including domain name permutations) to derive this.
Example: If phishing campaigns using harvested emails from an organization lead to widespread negative news or customer complaints, ThreatNG's brand damage susceptibility assessment would reflect this, indicating the impact of such activities.
Mobile App Exposure: ThreatNG evaluates how exposed an organization's mobile apps are by discovering them in marketplaces and analyzing their content for access and security credentials, including
mailtolinks.Example: If ThreatNG finds a mobile app related to the organization containing hardcoded email addresses or
mailtolinks that could be easily scraped would flag this as a mobile app exposure.
Reporting
ThreatNG provides diverse reporting capabilities that are critical for understanding and addressing the risks of email address harvesting:
Security Ratings (A through F): The overall security rating would reflect the aggregated risk, including factors influenced by email harvesting susceptibility.
Prioritized Reports (High, Medium, Low, and Informational): Findings related to exposed email addresses, weak email security configurations, or compromised credentials would be categorized by risk level, allowing organizations to focus on the most critical issues first.
Executive and Technical Reports: These reports would provide tailored views for different audiences, explaining the impact of harvested emails on the organization's security posture and offering actionable insights.
Ransomware Susceptibility Report: This report highlights how harvested emails can be used as an initial vector for ransomware attacks, especially when combined with compromised credentials.
Continuous Monitoring
ThreatNG continuously monitors an organization's external attack surface, digital risk, and security ratings. This continuous monitoring ensures that:
New Exposures are Detected: If new email addresses are inadvertently published or if a new data breach exposes organizational credentials, ThreatNG would detect these changes in near real-time.
Risk Posture is Up-to-Date: The security ratings and risk assessments are constantly updated to reflect the current threat landscape and the organization's evolving digital footprint.
Alerts are Generated: Organizations can be immediately alerted to critical findings, such as a surge in exposed email addresses or compromised credentials, allowing for rapid response.
Investigation Modules
ThreatNG's investigation modules provide deep insights that help pinpoint the sources and extent of email address exposure:
Domain Intelligence:
Email Intelligence: This module provides explicit support for "Security Presence (DMARC, SPF, and DKIM records)" and "Format Predictions, and Harvested Emails."
Example: A user could use this module to see how many email addresses associated with their domain have been "harvested" and are known to ThreatNG, or to verify if their DMARC, SPF, and DKIM records are correctly configured to prevent email spoofing.
WHOIS Intelligence: This module can reveal email addresses listed in WHOIS records for domain registrations.
Example: An investigator could use WHOIS Intelligence to identify generic contact emails for their domains that harvesters might target.
Subdomain Intelligence: This module identifies
EmailsandPhone Numberswithin subdomain content.Example: If a long-forgotten development subdomain contains a test page with an email address, Subdomain Intelligence would uncover this.
Archived Web Pages: This module specifically discovers
Emailswithin archived web content.Example: An organization could use this to determine if historical versions of their website, archived in web archives, contain outdated employee email addresses that are no longer active but could still be harvested.
Sensitive Code Exposure: This module discovers public code repositories and investigates their contents for sensitive data, including
Mailtolinks and variousAccess CredentialsandSecurity CredentialsThat could be related to email accounts.Example: If a developer accidentally pushes code containing an API key or an explicit email address to a public GitHub repository, ThreatNG would find this under "Code Repository Exposure."
Dark Web Presence: This module identifies explicitly "Associated Compromised Credentials" linked to the organization.
Example: An analyst could utilize this module to identify instances where organizational email addresses, particularly those of executives, have been exposed in data breaches on the dark web, indicating high-value targets for harvesting and subsequent attacks.
Search Engine Exploitation: This module helps users investigate an organization’s susceptibility to exposing "User Data" and "Errors" via search engines. It also specifically discovers
Emails FoundinRobots.txtandSecurity.txtfiles.Example: ThreatNG could show if search engines have indexed pages containing email lists or contact details that were mistakenly not excluded by
robots.txtfiles.
Intelligence Repositories (DarCache)
ThreatNG's continuously updated intelligence repositories, branded as DarCache, provide critical context for understanding email address harvesting threats:
Compromised Credentials (DarCache Rupture): This repository contains information on compromised credentials, which are often email addresses paired with passwords. This is directly relevant to identifying which harvested emails might be most dangerous.
Example: If an organization's domain email addresses appear frequently in DarCache Rupture, it indicates a high likelihood of successful phishing or account takeover attempts if those harvested emails are used.
Ransomware Groups and Activities (DarCache Ransomware): Ransomware attacks often begin with phishing emails, making knowledge of active ransomware gangs and their tactics valuable.
Example: By cross-referencing harvested email addresses with intelligence from DarCache Ransomware, an organization could identify if certain email addresses are being targeted by known ransomware groups.
Vulnerabilities (DarCache Vulnerability): While not directly about email harvesting, this includes NVD, EPSS, KEV, and Verified Proof-of-Concept (PoC) Exploits. If systems storing email addresses (e.g., mail servers, CRM systems) have known vulnerabilities, harvested emails become more dangerous.
Example: If ThreatNG identifies that an organization uses an outdated email server software with a known critical vulnerability (from DarCache NVD or KEV), and that vulnerability has a high EPSS score (from DarCache EPSS) indicating a high likelihood of exploitation, this would elevate the risk associated with any harvested email addresses from that system.
Complementary Solutions
ThreatNG's capabilities can be significantly enhanced when used in conjunction with other cybersecurity solutions, creating a more robust defense against email address harvesting and its downstream impacts:
Email Security Gateways (e.g., Proofpoint, Mimecast):
Synergy: ThreatNG's ability to identify exposed email addresses, predict email formats, and assess BEC/Phishing susceptibility directly informs the configuration and effectiveness of email security gateways. ThreatNG can identify which email addresses are most likely to be targeted (e.g., those found on the dark web or with compromised credentials ). The email security gateway can then prioritize filtering, implement stricter policies, and apply advanced threat protection for those specific addresses or user groups.
Example: ThreatNG identifies a significant number of executive email addresses from a recent dark web dump. This intelligence is then used by the email security gateway to apply highly aggressive anti-phishing and anti-spoofing policies specifically to emails sent to or appearing to be from these compromised accounts.
Security Information and Event Management (SIEM) / Security Orchestration, Automation, and Response (SOAR) Platforms:
Synergy: ThreatNG's continuous monitoring and detailed assessment findings, especially those related to data leaks and compromised credentials, can feed into a SIEM for correlation with other logs. A SOAR platform can then automate responses.
Example: ThreatNG detects a new instance of exposed email addresses and associated sensitive data on a public code repository. This alert is sent to the SIEM, which correlates it with internal network traffic logs. The SOAR platform then automatically triggers a workflow to notify the development team, block access to the repository, and initiate a password reset for affected users, leveraging ThreatNG's specific findings on access credentials.
Identity and Access Management (IAM) Solutions:
Synergy: ThreatNG's "Dark Web Presence" and "Compromised Credentials" intelligence can directly inform an IAM solution. If ThreatNG discovers that user email addresses and passwords have been harvested and are available on the dark web, the IAM system can enforce immediate password resets, multifactor authentication (MFA) requirements, or temporarily suspend accounts, reducing the risk of account takeover.
Example: ThreatNG's DarCache Rupture indicates that several user email addresses have been compromised. The IAM solution is then triggered to force MFA for all logins associated with those email addresses and prompt for a mandatory password change upon the next login.
Threat Intelligence Platforms (TIPs):
Synergy: While ThreatNG has its own robust intelligence repositories, it can ingest or share data with other TIPs to enrich context. For instance, ThreatNG's identified harvested emails or specific attack patterns (e.g., from BEC & Phishing Susceptibility ) could be shared with a TIP to identify broader campaigns or threat actor TTPs. Conversely, a TIP might provide context on new harvesting tools or techniques that ThreatNG could then prioritize in its external discovery.
Example: ThreatNG identifies a rise in email format predictions being used for a specific phishing campaign. This information is fed into a broader threat intelligence platform, which correlates it with observed threat actor activity, providing a richer understanding of the campaign and enabling more proactive defenses across different security tools.
By combining ThreatNG's external, attacker-centric view with the internal visibility and enforcement capabilities of complementary solutions, organizations can establish a robust defense against email address harvesting and its subsequent exploitation.