December 19, 2025
From Hidden Sprawl to Boardroom Confidence: Reclaim Your "Invisible Attack Surface
We are proud to introduce a groundbreaking upgrade to the ThreatNG platform, designed to give CISOs and executive leaders complete control over the "Invisible Attack Surface." This release addresses the "Contextual Certainty Deficit," the overwhelming gap where you know a threat exists but lack the undeniable, board-justified evidence to act. By delivering Legal-Grade Attribution, we turn technical noise into a clear governance directive, shifting your organization from uncertainty to decisive, proactive leadership. Existing users are encouraged to log in now to see their new security ratings. Meanwhile, all of the forward-thinking leaders eager to go beyond simply "checking boxes" and start securing their legacy should contact us today for a free assessment.
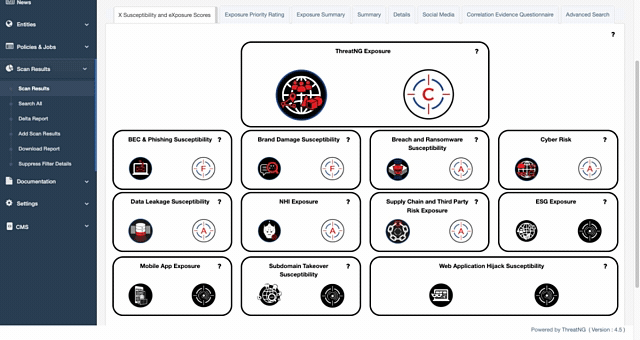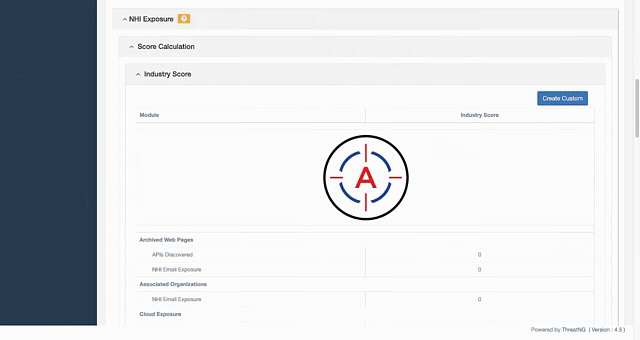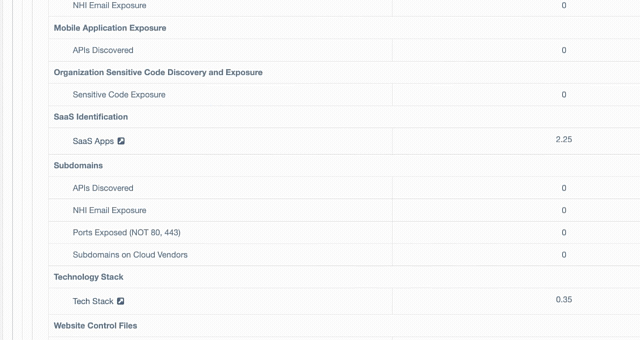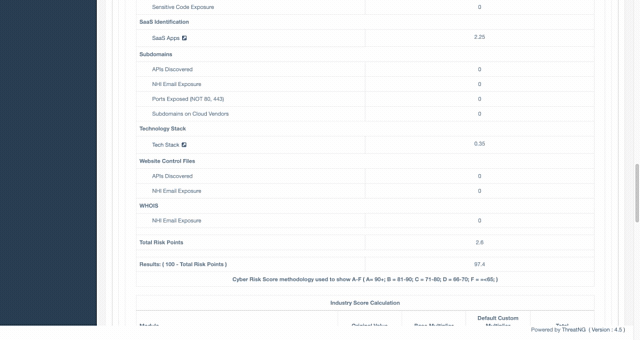
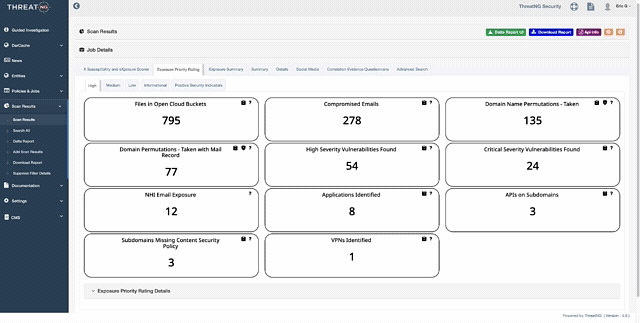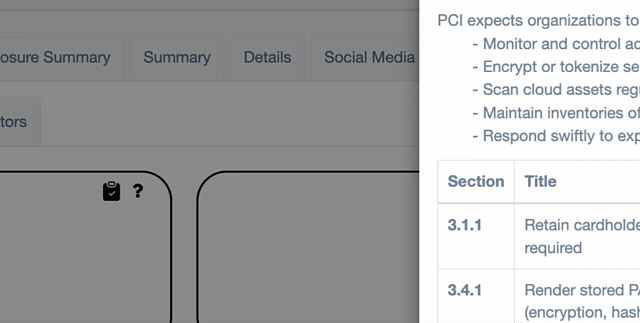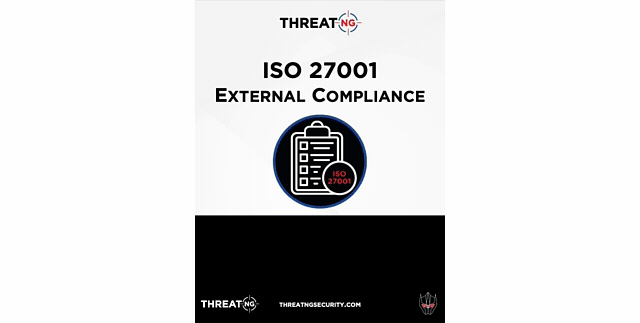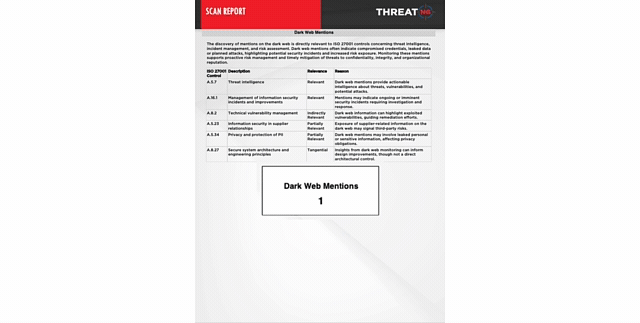
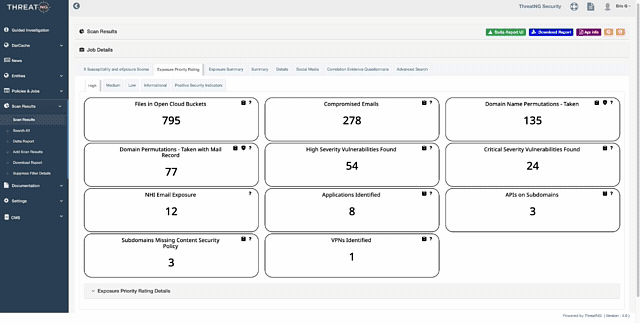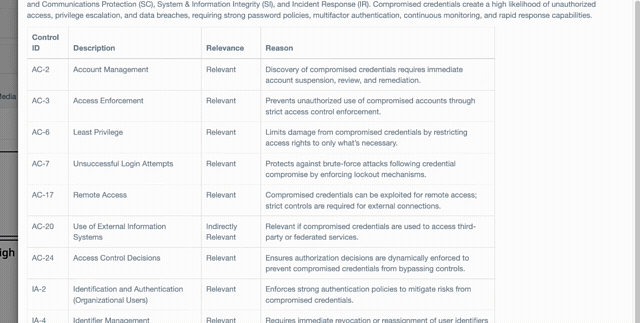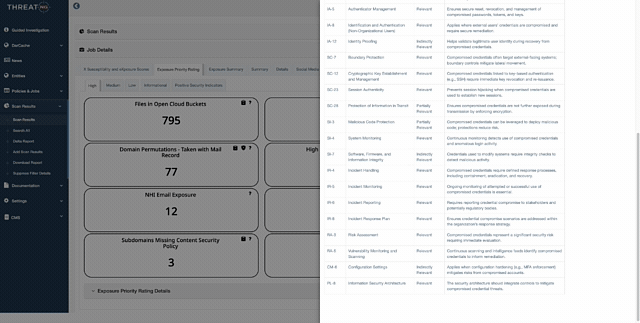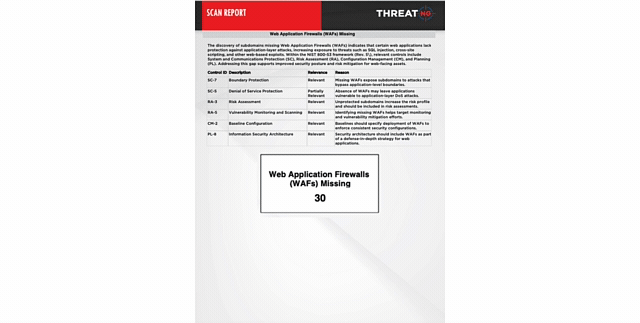
Master the Unseen: The Industry’s First External NHI Exposure Security Rating
The modern enterprise is being hollowed out by "Non-Human Identity sprawl," a silent explosion of service accounts and API keys that traditional tools cannot see. ThreatNG’s groundbreaking NHI Exposure Security Rating acts as your proactive shield, using purely external, unauthenticated discovery to mimic exactly what an adversary sees. We eliminate the "Fear of the Unknown" by identifying active, high-privilege machine identities and providing an objective A-F rating you can take directly to the board to justify critical security investments. Stop the "Hidden Tax on the SOC" and transform days of manual log-chasing into minutes of decisive remediation.
Beyond Paper Thin: Continuous ISO 27001 Resilience Validation
Don't let your organization fall victim to the crisis of being "compliant-yet-vulnerable". While traditional audits offer only a static, reactive "snapshot" of security, our new External ISO 27001 Assessment provides continuous, data-driven validation that proves you are truly resilient, not just compliant on paper. By automatically mapping live external exposures, such as orphaned DNS records or open cloud buckets, directly to ISO 27001 mandates, we provide the "provable chains" of evidence required for high-stakes fiduciary oversight. This is your path to audit-ready certainty, reducing your Mean Time to Detect (MTTD) by up to 80% and fulfilling your duty to protect shareholder value from catastrophic brand damage.
Adversarial Assurance: Rigorous NIST 800-53 Compliance Mapping
In the high-stakes world of federal revenue and FedRAMP authorization, the "distance" between documented policy and the actual defensive posture can be a multi-million-dollar disaster. ThreatNG’s External NIST 800-53 Assessment replaces manual spreadsheets with irrefutable evidence, proven from the adversary's perspective. Whether you are a Cloud Service Provider seeking to avoid the "$25 million swing" of non-compliance or a CISO eliminating configuration drift, our platform identifies technical truths that contradict internal baselines. Empower your GRC teams to trade manual "evidence hunts" for automated Security Assessment Reports, ensuring your fortress is validated by reality rather than theory.
Ready to witness your true external security posture?
Existing Users: Log in now to view your new NHI Exposure Rating and GRC Dashboards.
New Partners: Contact us today for a free, no-obligation evaluation and stop gambling on your compliance.