January 7, 2026
Master the Adversarial Narrative: Reclaim Strategic Calm with Contextual Intelligence
You have followed every industry best practice, investing millions in a security stack with more than 20 tools and ticking every framework box, yet the "Perpetual Crisis Posture" persists. You are battling a "Hidden Tax on your SOC," where exhausted analysts lose 30 minutes per siloed alert while the true breach narrative unfolds in your blind spots. This latest release marks a fundamental shift from reactive chaos to Strategic Calm. We are moving beyond static lists of vulnerabilities to provide you with Legal-Grade Attribution and predictive storytelling, empowering you to disrupt an attacker’s sequence before they ever reach your most valuable assets. Log in now to the ThreatNG Platform (platform.threatngsecurity.com) to reclaim your team’s time, or contact us today for a Free Evaluation to see your organization exactly as a motivated adversary does.
ThreatNG DarChain: From Static Alerts to Predictive Storytelling
Stop managing isolated findings and start mastering the adversary’s narrative. DarChain (Digital Attack Risk Contextual Hyper-Analysis Insights Narrative) is a proprietary engine that "chains" disparate technical, social, and organizational findings into a 3D view of the exact paths a breach would take. By identifying "Choke Points," which are critical nodes where multiple attack paths intersect, you can achieve a 10x security impact by breaking the chain at its most vulnerable stage. Experience the relief of moving from the exhaustion of "patching everything" to the strategic certainty of knowing exactly which external path leads to your crown jewels.
The Reconnaissance Hub: Your Unified Command Center for Absolute Certainty
Abolish the "Hidden Tax on your SOC" with the Reconnaissance Hub, the industry’s first unified interface engineered to bridge the "Attribution Chasm". This command center transforms passive monitoring into active, intelligence-led investigation by fusing technical findings with decisive legal and operational context. It provides the "Certainty Intelligence" required to justify every security investment and remediation request with absolute confidence.
Overwatch (Search All): Gain an all-seeing, portfolio-wide vantage point to instantly find a specific CVE, vendor, or technology across all managed clients, vendors, and subsidiaries in minutes rather than days.
Advanced Search: Perform deep-dive, granular investigations into a single entity's attack surface to pinpoint specific frameworks and technologies for forensic analysis.
DarChain (Attack Path Intelligence): Trace interconnected data fragments, such as leaked credentials and forum mentions, to uncover the hidden relationships between external threats and your digital assets.
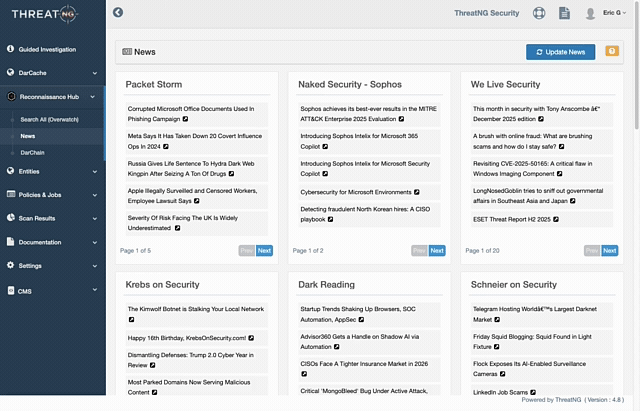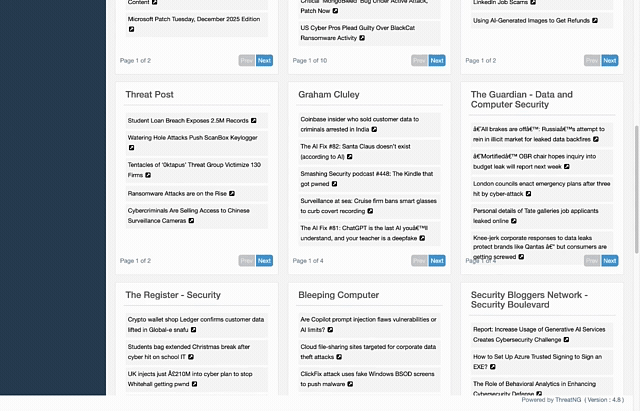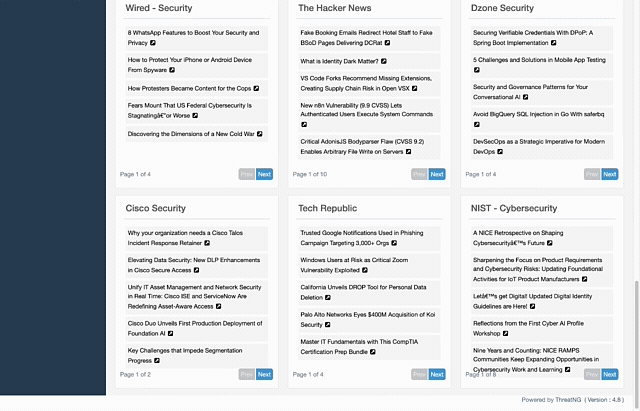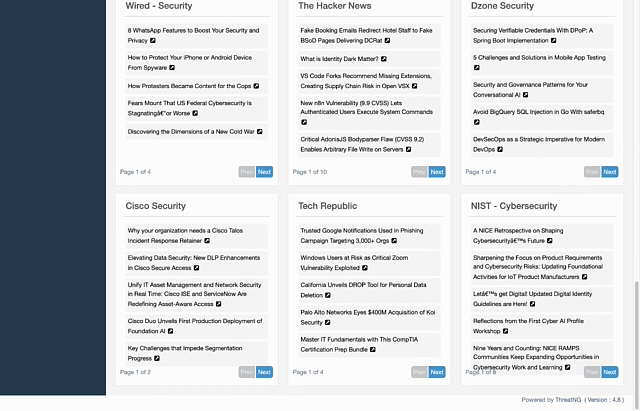
Cybersecurity News Feeds: Use live, curated intelligence that automatically correlates global threat news with your unique digital footprint to end the exhausting manual triage marathon.
The Power of the Hub in Action: A Story of Strategic Calm
Imagine a morning where the News Feed alerts you to a trending exploit used by a major ransomware group. Instead of panic, you use Overwatch to instantly scan your entire global portfolio, identifying three subsidiaries and two critical vendors currently using that specific vulnerable technology. You pivot to Advanced Search on the most vital subsidiary to uncover a forgotten subdomain that internal tools missed.
Next, you run DarChain, which reveals a terrifying narrative: an attacker could use a leaked employee email (Social) found on the dark web to target that unpatched VPN (Technical), creating a direct path to an open cloud bucket containing sensitive financial records. Within minutes, you identify the "Choke Point" and patch that one subdomain that breaks the entire chain. You present this as Legal-Grade Attribution to the Board, showing them the "movie" of the attack before it happens and confirming that the threat has been neutralized before it ever reached the headlines.
DarCache Ransomware Intelligence: Ending the Contextual Certainty Deficit
In an era where the stakes of a breach are personal, and 56% of CISOs feel personally blamed for failures, DarCache Ransomware transforms you from a "scapegoat" into a hero of operational resilience. This sanitized, queryable repository monitors over 100 ransomware gangs and their real-time TTPs, replacing three-day manual "fire drills" with seconds of queryable certainty. Whether you are facing "Big Game Hunters" or "Extortion Specialists," DarCache provides the Legal-Grade Attribution needed to satisfy the Board and regulators with irrefutable, observed-fact proof rather than hypothetical risks.
DarCache ESG Intelligence: Unmasking the Invisible Link to Cyber Risk
Redefine your risk management by bridging the gap between ESG performance and cybersecurity. DarCache ESG is a cutting-edge repository that correlates global ESG violations—such as financial misconduct or environmental penalties—with your external attack surface. This capability acts as an early warning system; for example, an ESG controversy can often attract the attention of specific hacktivist groups. By using this intelligence, you can uncover hidden liabilities in your supply chain and protect your brand reputation by anticipating narrative-driven attacks before they mature into technical breaches.