February 12, 2026
From Operational Anxiety to Strategic Calm: The Era of Contextual Certainty is Here
You are not suffering from a lack of data; you are suffering from a surplus of noise. In a landscape where the gap between "technical vulnerability" and "business catastrophe" is widening, traditional security tools have left you in a state of operational paralysis. The latest release from ThreatNG is designed to act as your Strategic Risk Architect. We are moving beyond mere observation and into the era of Legal-Grade Attribution. Whether you are facing the pressure of a four-day SEC disclosure window or the existential threat of fiduciary liability, these enhancements provide the unshakeable evidence you need to lead with confidence.
External SOC 2 Assessment: Bridge the Compliance Gap with Unshakeable Certainty
Stop guessing if your security reality matches your policy paperwork. While traditional GRC tools leave you audit-ready only on paper, External SOC 2 Assessment uses continuous, "outside-in" discovery to unmask the "Machine Ghosts" and Shadow IT that lead to audit failure. By automatically mapping technical findings like dangling DNS and exposed cloud buckets directly to SOC 2 Trust Services Criteria, we transform compliance from a reactive fire drill into a proactive defense of your professional reputation.
Existing Users: Log in now to see how your external footprint aligns with SOC 2 standards.
New Users: Don't wait for an auditor to find your gaps. [Contact us today for a free evaluation] and experience the power of Contextual Certainty.
External DPDPA Assessment: Shield Your Fiduciary Legacy from the ₹250 Crore Risk
In the Indian market, cybersecurity is no longer just an operational hurdle; it is a matter of strict liability. This assessment acts as the "antidote to shelfware," providing a purely external, "No Connector" view of the liabilities that could trigger non-negotiable financial penalties. The External DPDPA Assessment identifies high-stakes exposures, such as open cloud buckets and subdomain takeovers, before they become a ₹250 Crore headline. Gain the "Legal-Grade Attribution" necessary to protect your Board and your career from personal liability.
Existing Users: Your DPDPA assessment module is live. Log in to validate your "reasonable security safeguards" immediately.
New Users: Ignorance of the attack surface is corporate negligence. [Contact us for a free evaluation] to secure your digital borders.
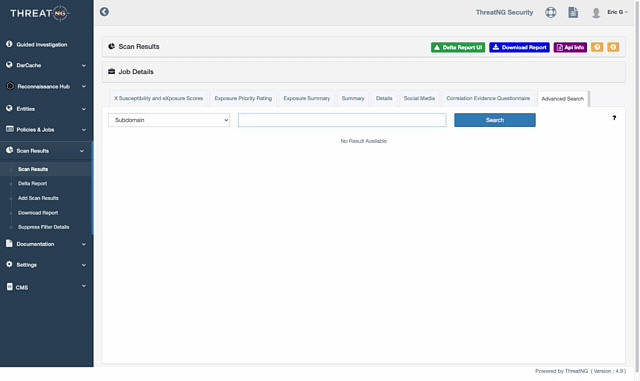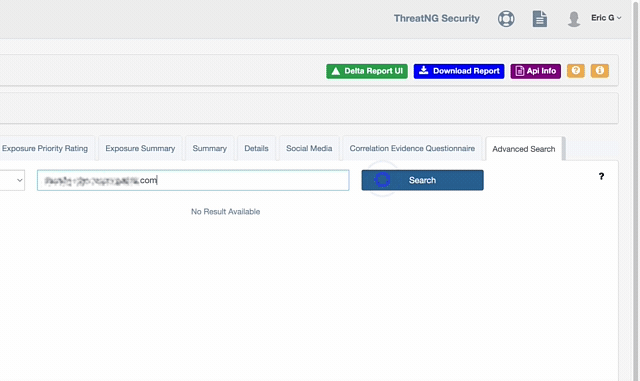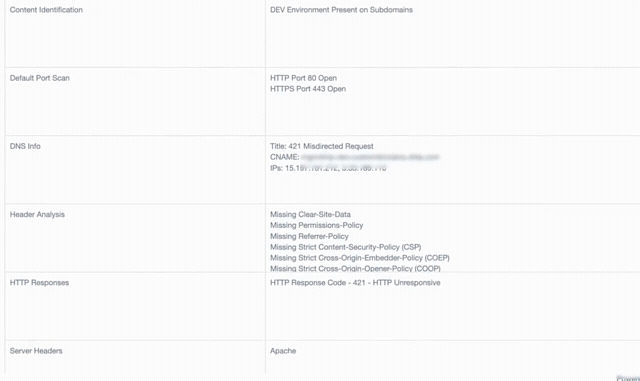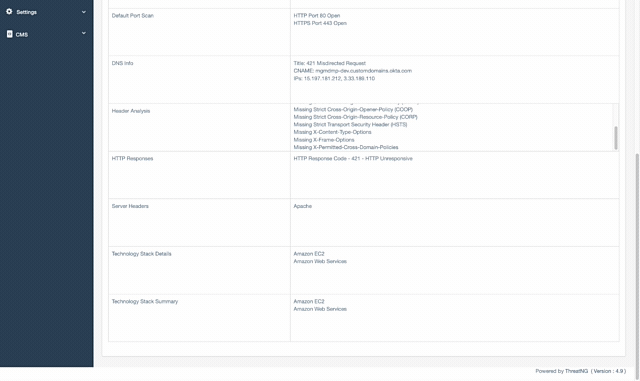
Enhanced Subdomain Advanced Search: Unmask Your Assets with Legal-Grade Attribution
The "Contextual Certainty Deficit" ends here. This enhancement transforms our Subdomain Search into a "Truth Engine" that validates ownership and business function in real-time. Designed specifically for the high-pressure SEC four-day materiality window, Subdomain Advanced Search allows you to instantly distinguish between a legitimate corporate asset and a rogue "Unknown Unknown." Eliminate the "Hidden Tax" of manual investigation and proactively dismantle attack paths before an adversary can use them to exploit your organization.
Existing Users: Experience the enhanced search in the Reconnaissance Hub today to verify your asset ownership.
New Users: Stop chasing ghosts in your DNS. [Schedule your free evaluation] to see your true adversary view.
DarCache Vulnerability: Abolish the Noise with the Strategic Risk Architect
Replace the anxiety of "patching everything" with the confidence of solving what matters. Our enhanced 4-Dimensional Data Model provided within our Vulnerability Intelligence Repository (DarCache Vulnerability) cross-queries NVD, EPSS, KEV, and verified Proof-of-Concept (PoC) exploits to deliver a "Decision-Ready" verdict, not just another list of flaws. By using verified PoCs as a "Truth Serum,” we help you ignore the theoretical noise and focus on the functional, weaponized threats that pose a real-world risk to your business valuation.
Existing Users: Log in to access your new Risk Verdicts and stop the "Hidden Tax" on your SOC analysts.
New Users: Move from reactive panic to strategic hunting. [Contact us for a free evaluation] to see which vulnerabilities are actually weaponized against you.